Cyberbullying has many forms and can include a variety of acts. It can be sending a mean text message, making online threats, sending unwanted provocative photos, posting insults or hate speech, attempting to infect the target’s computer with a virus, flooding an e-mail inbox with messages2 or sending harmful material and any other form of social aggression using the Internet or other digital technologies. Some of the most common cyberbullying tactics are briefly described below.
Cyberstalking: a bully repeatedly and intensively harasses, denigrates or threatens the target, enough to create fear.
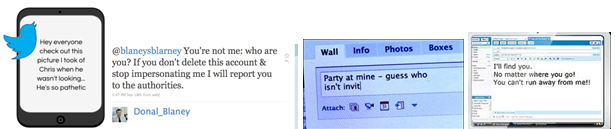
Cyberthreats: a bully makes threatening remarks on the internet or implies violent behaviour. It can also be threatening with suicide.
Denigration: a bully starts rumours about a person to damage their reputation. “Dissing” someone online.
Exclusion: a group of bullies excludes someone from online conversations, groups or from events shared online to hurt their feelings.
Flaming: a bully starts or fuels online fights exchanged through emails, instant messages, chat rooms or comments. There is often harsh language directed towards a specific person.
Harassment: a bully repeatedly sends or posts mean, hurtful or insulting messages or comments.
Masquerading/impersonation: a bully creates a fake identity to harass someone anonymously or impersonating somebody else to him send malicious messages or post material to get that person in trouble or danger or to damage that person’s reputation or friendships.
Outing: a bully shares someone’s secrets or embarrassing photos online.
Trickery: a bully tricks someone to share private information or photos with them and then shares this online.
Of course, this is just one way of classifying cyberbullying. You might find another model that helps you and the young people you are working with even better. But it is always useful to have some language and tools to think and talk about a problem. Take a look at some real life examples below and think about them. Can you identify types of cyberbullying in the following examples? What would you do if you came across one of these messages in real life? How could you talk to a sender of these messages? How could you talk to the recipient?
 |
Source: |