Hurting someone’s feelings, causing problems for them and making them feel bad are not new phenomena among young people. We would like to believe that we are teaching young people intra- and interpersonal skills that will help them feel confident in themselves as well as emphatic and respectful towards others, but the reality is that peer bullying has been a big challenge for schools, youth organizations, and local communities for many years. Is cyberbullying just a contemporary expression of this?
Studies are beginning to show3 that cyberbullying is very different from traditional schoolyard bullying. Some important differences are shown in the picture below.
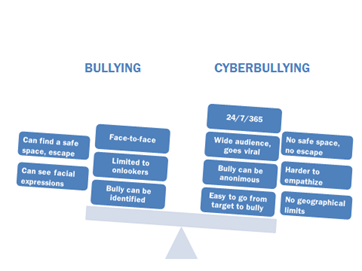
Traditional bullying is mostly pre-meditated, cyberbullying is often impulsive.
Research indicates that cyberbullying is rarely premeditated like traditional bullying.3 Cyberbullying is often done impulsively and not planned out like in traditional bullying where the bully plans the attacks.
Traditional bullying is more predictable, cyberbullying can happen anytime and anywhere.
Traditional bullying is usually limited to certain times and places, for example, the playground or the way to school. This gives the target some (although limited) sense of predictability, and there are times and places where he or she can feel safe. In contrast, technology is everywhere: we have our phones and computers around us all the time. Cyberbullying can happen 24 hours a day, 7 days a week and 356 days a year. It can happen in our close proximity or through great distances. It is difficult for the target to find a safe space.
Traditional bullying uses aggression and power to gain control; cyberbullying might not.
Furthermore, traditional bullying is characterized by the need for power and control, aggression and proactively targeting the target. These characteristics may not be present in cyberbullying cases.
Traditional bullying is done face-to-face, cyberbullying can be anonymous.
Cyberbullying is “an easier way to bully because unlike traditional bullying it doesn’t involve face to face interaction.”3 Hiding behind the computer decreases empathy the bully feels toward the target. When we do not see the person’s reaction to what we post or text them, we might not know that we have gone too far. Desensitized by the computer screen, it becomes easier to say or do things we would not do to a person’s face. Furthermore, while “traditional” bullies can mostly be identified, it can be very difficult to find out who the anonymous cyberbullies are, making it easier for bullies to avoid seeing and facing the consequences of their actions.
The roles in cyberbullying are usually not as clearly divided as in traditional bullying.
In traditional bullying, we are usually working with a bully, target or bystander. Although we often find that bullies have previously experienced violence themselves (perhaps when they were younger or by someone with more power), the roles in each case are pretty clear. This is not necessarily the case in cyberbullying. Young people often play multiple roles at once, such as cyberbully, target, and witness. There is also no clear-cut profile of who can be the cyberbully and who can be the target, it can happen to anyone.
Traditional bullying is done in secret; cyberbullying can go public and viral.
An especially problematic aspect of cyberbullying is that it often has many, many onlookers. Traditional bullying is more often done in private than in public. But in cyberbullying, technology makes it easy to quickly spread content to a large number of people. Online bullying can quickly become very public or even viral. This wide audience makes the experience especially difficult and embarrassing for the target.
Traditional bullying seems to have clearer predictors and risk factors than cyberbullying.
Current research in public health indicates that many “social” factors such as education, socioeconomic conditions, access to services and resources, family ties, employment etc. are closely related to the person’s general health and mental health, including the ability to avoid or cope with violence and “traditional” bullying. Such connections with cyberbullying are less clear. It rather seems that there are no ‘typical’ cyberbullies and targets, it can happen to anyone. For example, it is well documented that in traditional bullying males are more likely to become bullies than females; that older adolescents are more likely to bully than preadolescents, and that bullies are more likely to have low than high self-esteem. For cyberbullying, on the other hand, age, gender or self-perception do not seem to be reliable predictors. Interestingly, high-quality relationships with important adults seem to be a strong protective factor in both types of bullying, traditional and cyber.


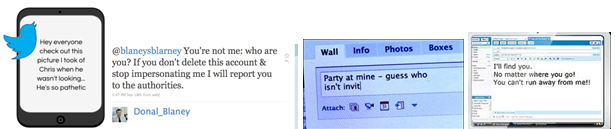

 Ashley lives in Colorado and has been growing up like any other teen, being influenced by her peers as much as she’s influenced by her parents’ guidance. However, she never expected how invasive the Internet could be without her knowing about it or even having a say in the matter. In Ashley’s case, the bullying that occurred may seem benign on the surface, but it had the potential to be far more.
Ashley lives in Colorado and has been growing up like any other teen, being influenced by her peers as much as she’s influenced by her parents’ guidance. However, she never expected how invasive the Internet could be without her knowing about it or even having a say in the matter. In Ashley’s case, the bullying that occurred may seem benign on the surface, but it had the potential to be far more.





 Jessica Logan was an 18-year-old high school senior who sent nude photos of herself to her boyfriend. After the couple broke up the boyfriend sent the photo that was meant for his eyes only to hundreds of other teenagers via group chats. The photo sharing led to name calling and taunts at school. Phrases like “slut, porn queen, and whore” were regularly spoken referring to Jessica by schoolmates. The taunting continued via Facebook and through text messages.
Jessica Logan was an 18-year-old high school senior who sent nude photos of herself to her boyfriend. After the couple broke up the boyfriend sent the photo that was meant for his eyes only to hundreds of other teenagers via group chats. The photo sharing led to name calling and taunts at school. Phrases like “slut, porn queen, and whore” were regularly spoken referring to Jessica by schoolmates. The taunting continued via Facebook and through text messages. At the beginning of the school year, Sara moved into a new school. At first, things were great and Sara was very popular. However, after a couple weeks at her new school, her parents noticed that she seems depressed and anti-social. They observe that she rarely socializes with her friends. Sara’s parents are worried about her and suspect that something is not quite right at school. They try to talk to Sara, but she is reluctant to talk. She tells them that she and her friends had an argument and are not getting along. Sara’s parents do not realize the problem is more dangerous than a disagreement between friends.
At the beginning of the school year, Sara moved into a new school. At first, things were great and Sara was very popular. However, after a couple weeks at her new school, her parents noticed that she seems depressed and anti-social. They observe that she rarely socializes with her friends. Sara’s parents are worried about her and suspect that something is not quite right at school. They try to talk to Sara, but she is reluctant to talk. She tells them that she and her friends had an argument and are not getting along. Sara’s parents do not realize the problem is more dangerous than a disagreement between friends. Gina, an exuberant and spirited high school freshman, had a falling out with a girlfriend over a boy they both liked at school. It wasn’t long before Gina began getting rude text messages to her phone at all hours, calling her names and saying inappropriate things such as, “I hope you die soon.” The angry friend had enlisted others to text hateful remarks to Gina too.
Gina, an exuberant and spirited high school freshman, had a falling out with a girlfriend over a boy they both liked at school. It wasn’t long before Gina began getting rude text messages to her phone at all hours, calling her names and saying inappropriate things such as, “I hope you die soon.” The angry friend had enlisted others to text hateful remarks to Gina too. Ryan Halligan was a 13-year-old middle schooler from Vermont who first experienced bullying in the fifth grade because of his poor physical condition. By the time he made it to seventh grade Ryan was begging his parents to home school him or if they could move. His parents contacted the school and tried to work out the issues. Boys at school started rumours that he was gay. Over the summer he worked on establishing a relationship with a popular girl from his school online. When he returned for his eighth grade year, and went to approach his girlfriend in real life, where she told him in front of all her friends he was a loser and that everything she had said to him online was a lie. The girl had copy/pasted all of their instant messages and sent them to a friend for a laugh at Ryan’s expense. Humiliated, Ryan took his life.
Ryan Halligan was a 13-year-old middle schooler from Vermont who first experienced bullying in the fifth grade because of his poor physical condition. By the time he made it to seventh grade Ryan was begging his parents to home school him or if they could move. His parents contacted the school and tried to work out the issues. Boys at school started rumours that he was gay. Over the summer he worked on establishing a relationship with a popular girl from his school online. When he returned for his eighth grade year, and went to approach his girlfriend in real life, where she told him in front of all her friends he was a loser and that everything she had said to him online was a lie. The girl had copy/pasted all of their instant messages and sent them to a friend for a laugh at Ryan’s expense. Humiliated, Ryan took his life. Henry was a shy sixth-grader who recently arrived at school from out of state. One day as he was browsing a social media site he came across a page about the school with pictures of students, including one of him labelled “The Fat Nerd.” Upset, he posted a reply expressing his dismay.
Henry was a shy sixth-grader who recently arrived at school from out of state. One day as he was browsing a social media site he came across a page about the school with pictures of students, including one of him labelled “The Fat Nerd.” Upset, he posted a reply expressing his dismay.