What does it mean to be at-risk of cyberbullying? This means that it is quite likely that someone might become involved in cyberbullying; either as a target, as a bully or as a bystander. In the last subchapter, we already mentioned some things that might put someone at risk of or protect them from bullying or cyberbullying.
Category: 3.4 Who is At-Risk?
3.4.1 What puts someone at risk and what protects them?
When we talk about at-risk groups for any problems that children and youth face, we like to think in terms of risk factors and protective factors: what puts someone at risk of unwanted things happening to them? What protects them from the problem or at least from suffering serious consequences? We understand many risk factors and protective factors that influence the physical and mental wellbeing of children and youth, their educational success, their relationships, their self-esteem, their future happiness, job prospects and their resilience to difficult events or other challenges.
For example, we know that children and young people, who face higher risks of becoming involved in ‘traditional’ bullying, often feel lonely, perceive their parents as distant and have problematic relationships with other adults in their lives like their teachers. They might have personal experience with violence in the family, peer group or other immediate environment. Many also have low self-esteem, poor social skills and communication skills. Traditional bullies are more likely to be male than female and more likely to be older adolescents than preadolescents. Targets of ‘traditional’ bullying, on the other hand, are likely to have low self-esteem, distinct physical features are also very common (for example short and weak, glasses, obesity, disability), they are also often less popular among their peers. A very strong protective factor for someone that is a target of traditional bullying, for example, is having a trusted adult that they can talk to about what is happening, or growing up in an environment where information and support are available.
This short sampling of risk factors and protective factors probably seems so self-evident that we do not even need to mention them! However, it is worth mentioning them because something interesting happens when we take a closer look at cyberbullying.
3.4.2 What are risk factors and protective factors in cyberbullying?
A number of studies and scholarly papers investigate which children and adolescents are most and least at risk of experiencing cyberbullying. Results are interesting and unexpected: when it comes to cyberbullying, there are almost no common risk factors except opportunity. Online access and unsupervised online time and technology use is clearly a ‘prerequisite’ for cyberbullying. However, not all forms of media usages raise the risk of experiencing cyberbullying. Children and adolescents who spend more time using their cell phone are more likely to report receiving aggressive or threatening electronic communication, but no such relationship seems to exist between time spent on the internet and either form of online bullying6.
Most studies find that age and gender do not have a very clear predictive role in cyberbullying. Some early research findings suggested that cyberbullies are often kids who were themselves bullied in real life. But later research found that cyberbullies and targets can just as well be popular, well-adjusted kids who have not been exposed to peer-aggression before. Whereas low self-esteem is usually linked to traditional bullying, many cyberbullies demonstrate a high perception of self-esteem in perceiving their relationships with peers as satisfying. However, feelings of loneliness and a perception of unsafety at school were often linked to cyberbullying.
In short, there seem to be very few common risk factors and even fewer protective factors that would prevent children and young people from becoming involved in cyberbullying. It really can happen to anyone. Research findings suggest that the most important protective factors against cyberbullying are strong parent relationships and positive experiences at school. Restrictions on media use enforced by adults were far less effective in fighting cyberbullying.6
However, although there are few risk factors that can help us predict involvement in cyberbullying and very few protective factors that would prevent children and young people from becoming involved, there are some important protective factors that can help them respond to cyberbullying resiliently. We might not be able to prevent cyberbullying from happening, but we can do things to minimize the damage so that the children and young people do not suffer prolonged or even life-threatening consequences. This can make a key difference in outcomes of cyberbullying both for the bullies and the targets.
Again, strong relationships among children and adults and positive school experiences are the strongest predictors of resilient response for children and adolescents who have faced cyberbullying. More specifically, students tended to behave resiliently if they:
- they could find an environment that felt emotionally and physically safe,
- had a trusted adult to talk to about problems,
- had parents of caretakers with basic digital competencies and awareness of online safety,
- experienced peer support and felt they are not alone in their experience,
- had access to practical information on what they can do to stop cyberbullying,
- had strong self-esteem, empathy, and social skills,
- were able (or given support) to cope with emotions, especially feelings of shame, guilt, sadness and fear.
Children and young people who have been onlookers are often at risk of perpetuating such behaviour. This is why it is so important to build healthy, empowering communities where cyberbullying does not go unrecognized, where such behaviour is talked about and challenged and where solutions for better relationships are found and invested in.
3.5 Types of Cyberbullying
Cyberbullying has many forms and can include a variety of acts. It can be sending a mean text message, making online threats, sending unwanted provocative photos, posting insults or hate speech, attempting to infect the target’s computer with a virus, flooding an e-mail inbox with messages2 or sending harmful material and any other form of social aggression using the Internet or other digital technologies. Some of the most common cyberbullying tactics are briefly described below.
Cyberstalking: a bully repeatedly and intensively harasses, denigrates or threatens the target, enough to create fear.
Cyberthreats: a bully makes threatening remarks on the internet or implies violent behaviour. It can also be threatening with suicide.
Denigration: a bully starts rumours about a person to damage their reputation. “Dissing” someone online.
Exclusion: a group of bullies excludes someone from online conversations, groups or from events shared online to hurt their feelings.
Flaming: a bully starts or fuels online fights exchanged through emails, instant messages, chat rooms or comments. There is often harsh language directed towards a specific person.
Harassment: a bully repeatedly sends or posts mean, hurtful or insulting messages or comments.
Masquerading/impersonation: a bully creates a fake identity to harass someone anonymously or impersonating somebody else to him send malicious messages or post material to get that person in trouble or danger or to damage that person’s reputation or friendships.
Outing: a bully shares someone’s secrets or embarrassing photos online.
Trickery: a bully tricks someone to share private information or photos with them and then shares this online.
Of course, this is just one way of classifying cyberbullying. You might find another model that helps you and the young people you are working with even better. But it is always useful to have some language and tools to think and talk about a problem. Take a look at some real life examples below and think about them. Can you identify types of cyberbullying in the following examples? What would you do if you came across one of these messages in real life? How could you talk to a sender of these messages? How could you talk to the recipient?
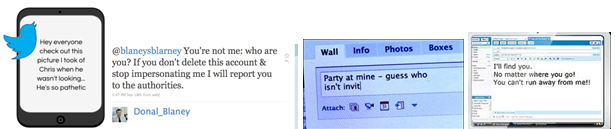
 |
Source: |