![]()
 |
 |
Editor: Matej Cepin
Authors: Matej Cepin, Urška Slana, Beate Roggenbuck, Valborg Edert, Mathias Kaps, Giacomo Trevisan, Mojca Galun
![]()
 |
 |
Editor: Matej Cepin
Authors: Matej Cepin, Urška Slana, Beate Roggenbuck, Valborg Edert, Mathias Kaps, Giacomo Trevisan, Mojca Galun
Newspapers and website are full of articles relating to problems and weaknesses of the educational system.
The recently deceased former associate editor of the Frankfurter Allgemeine Zeitung, Frank Schirrmacher, writes in his book “Minimum (2006)”: “… our children have fewer friends than previous generations. So not only the lives of individuals radically changed, but our society is reprogrammed insidiously; …. More and more we will be on our own, but alone we can not survive. At a time when the most valuable asset is its social capital – as we are forming new communities? … We are not prepared for the minimum of social relations. We suddenly standing in front of the original question a society: What is a family? How is trust? Who help whom? ”
These questions are quite interesting and pretty related to what we have been experiencing so far as Starkmacher association. One consideration came into my mind:
For this reason, the target group of our activities and our allegiance should not be only the young people. These latter certainly live in large transitional situations and struggle in finding their own position, their place in the society. However, equally important are the teachers in the schools, the social workers in youth and educational institutions, youth leaders and educators who often drag with a steadfast passion and against a negative opinion wave to the concerns of young people into the field.
Most of my colleagues are extremely committed and involved in activities targeting youth, and yet many of them feel overtaxed and alone. Teachers further of the transfer of knowledge are increasingly taking on educational tasks, which is no longer provided by parents or families. I was really surprised when I heard about teachers from the Berlin Rütli School (Berliner Morgenpost, 21.08.11 education crisis) who literally “gave up” because of the lack of ability to communicate in many schools. In recent years, working with teachers all around Europe, what I have been experiencing and witnessing is resignation and helplessness. It is a devastating feeling, leaving no room for improvements and no hope since these teachers are the ones our future generations will learn trust and confidence from. Therefore, it is not easy to find good and positive climates in the schools. This directly links to the violence and bullying I have witnessed in many schools. This behaviour translates into powerlessness and insecurity, and a great need for help.
Since 2003, along with friends and colleagues, we have been promoting a shared vision to tackle these challenges. Our wish was to combine our successful projects, exchanging so good practices and results, as well as difficulties and challenges in order to come up with new common effective projects. This was the inception phase of Starkmacher e.V. This latter was born in 2006 and it is currently based in Mannheim, with 5-7 permanent employees and numerous partners and volunteers from all around the world.
In the last years, Starkmacher has sustained more then 50 schools. Our approach has been focusing on the quality of the schools, in terms of climate, positivity , talent-oriented pedagogy and joyfulness. Unfortunately, most of the times we met a deficit-oriented approach, missing so the chances to empower the students, discover and appreciate their talents and positively make them active actors of the schools. Children from all around the world need to be sustained and guided with the hand in order to promote their holistic growth.
This thought is not new. Particularly in private schools or high schools there is a wide range of additional services and programs designed to promote students’ individual talents and abilities. However, disadvantaged students are often dropped by the wayside. At the same time, teachers are under enormous pressure to meet the demands of parents, Ministry and the public opinion.
Starkmacher projects perfectly match these challenges, targeting accurately teachers, pupils and families. The starting point of Starkmacher principle is: “The change starts from me: only when I, myself am strong, I can make others stronger”. Starkmachers’ projects create spaces of experience, in which individuals are strengthened and can experience being part of a community and the extreme importance of this latter.
Our approach has been developed establishing trustful relationships with teachers and, generally speaking, the administrative body. We bring everybody into the boat, to navigate the challenges and chances all together. This is an empowering exercise a “Starkmacher” exercise, in which everybody, teachers and pupils, those pretty much involved and those left out, feel being part of a unique and strong body.
The challenges and issues raised by new forms of bullying in schools are of concern to Starkmacher and its partners. Together, as a consortium, we came up with a project called “Joining Forces to Combat Cyberbullying in Schools”, with the main goal of creating “cyberbulling free schools”: the project was carried out by 8 NGOs from 5 EU Member States (DE, IT, PL, SI, HU) which closely cooperated with local partner schools. The implementation started by offering trainings to NGO staff from partner organisations in Conflict Resolution, Training of Trainers as well as new Social Media Management. The second strand was capacity building in schools, which was executed by the trained multipliers from a partner organisation. This included information and awareness raising activities with teachers/educators, school management, and parents in order to raise their awareness about the issue of cyberbullying and to increase new media know-how and critical awareness. It also intended to conduct local trainings on conflict resolution and social media competence with pupils and teachers, establishing so mediation clubs in each partner schools that shall provide trainings as well as peer mediation.
The second year was characterised by an individual empowerment of youth through creative social media. Organising Int’l Media Camps and local Creativity Groups helped in familiarising youngsters with respectful and safe media usage, but also unlocking hidden potentials, helping to promote a mentality of non-violence and respect in partner schools. After the 1st int’l workshop, the partner started local creativity contests for youngsters in order to produce new artworks. The winners have been then invited to the second int’l workshop. The final stage focused on awareness raising through a youth-led social media campaign helping to spread “anti-cyber violence messages to a widest possible public audience and especially younger people. The official launch of the campaign was on 20th November 2016, which marks the Universal Children’s Day.
In the following chapter, we are going to talk about Cyberbullying and which ways of intervention and prevention are known.
Our holistic approach will be described by Matej Cepin talking about our goal of changing school cultures towards bullying-free zones, through addressing the challenge of cyberbullying from many different angles, through the combination of different action. We believe our approach is Holistic (promotion / prevention / intervention, determinants of health), Community oriented (teachers, pupils, parents) and able to develop competencies through an active participation of stakeholders. Our actions and supportive actions (training of multipliers, creativity campuses, social media campaign) will be extensively described in the different paragraphs.
Finally, we will provide the readers with useful guidelines on how to implement the project in different schools and environments.
Let yourself embark on this journey! Look around and get involved with us for young people who need your encouragement!
Within this chapter, we will try to put in context the phenomenon of social networks within integrated development of a young person. First, we will define elementary terms and changes that incorporation of social media into our lives brings. The last subchapter discusses whether social media is harmful or stimulating for young people and what are the advantages and disadvantages. We will also reveal the truth behind prejudices and stress, how the lifestyle of young people is changing because of social media.

Social media = “forms of electronic communication (such as Web sites) through which people create online communities to share information, ideas, personal messages, etc.” (Merriam-Webster’s Learner’s Dictionary)
Young people discovered social media first. But now also adults can’t imagine life without social media. It became our way of communication, branding ourselves through online personas, building online communities and just spending free time. Whether it’s Facebook, Google+, Instagram Snapchat or some other social media app, it is slowly but firmly incorporating into every aspect of our lives.
The Rise of Social Media (Ben Brommell)
“Social networking is the practice of expanding the number of one’s business and/or social contacts by making connections through individuals.” (Whatis.com)
Social Networking in Plain English(Common Craft)
You’re asking what is the difference between Social media and social networking?
To make it simple social media is the way to connect (more of a one-way communication) and social networking mean building relationships (two-way communication). Read more about the difference in a blog of Fauzia Burke at Huffingtonpost.
 Source: Brian Solis & JESS3
Source: Brian Solis & JESS3
If you are new to the field of social media, we recommend to check out online dictionaries:
Every year the number of social media users is increasing and Statista is predicting that in the year 2020 the number of users will increase from 2,14 billion to almost 3 billion people.
There are so many different social media and last few years Facebook is the most used one.
And with that many people online and with the consideration that an average human spends 1.72h online, no wonder facebook and other social media is one of the biggest sources of information these days.
With a regular use of social media, many aspects of everyday life changed. First of all, we changed the way we communicate. It would be completely unheard if you would leave in the middle of a telephone conversation, but it is completely normal to leave while chatting and respond the next day. With different communication, styles came also changes in socialization process and community building styles.
How Social Networks Have Changed The World! (Alex Moore)
Modern technology has brought us many things: from easy access to information and quicker communication to increasing loneliness, from improving our productivity and efficiency to job losses and it made so many changes that sometimes it is hard to point a finger and decided whether we benefited as a society or it just brought us new problems in with that changed reality. But for sure it had a direct result in the availability of enormous quantities of data. Availability of big data is influencing the way we think and study and extracting knowledge from it will become more and more important.
Did You Know 2016 (mesjms)
Big data = “an accumulation of data that is too large and complex for processing by traditional database management tools” (Merriam-Webster’s Learner’s Dictionary)
“Modern technology is simply an advancement of old technology, the impact of technology in modern life is unmeasurable, we use technology in different ways and sometimes the way we implement various technologies ends up harming our lives or the society we leave in. What we call modern technology is technically not so new in most cases.” (Use of technology)
As the previous video said, we are currently preparing students for jobs that doesn’t exist jet, using the technology that hasn’t been invented jet in order to solve problems we don’t know they are problems jet. So the only thing we can really predict for future is that we have no idea what to predict. We can only guess about new trends that are coming.
Social Media Trends for 2016 (MtoM Consulting, LLC)
Social media influences each single individual that uses it. Widespread use has resulted also in influencing and changing the whole society.
As any new change social media has some advantages and some disadvantages. It is easy to see just one side, but nothing is black and white, so we would like to present both.
Social Media: Advantages and disadvantages (krismarfil)
Positive influences:
Negative influences:
Marc Maron: The Social Media Generation Animated (Jess the Dragoon)
Global spread of social media has enabled increased access to information and education to millions of people, which empowered them to become part of political processes in their societies. Voices that could not be heard in governmental and other mainstream media are suddenly given a chance to address wide audiences. Even people not keen on active political participation have become political actors by supporting and sharing those newly empowered voices on social media. This new dynamic puts unprecedented pressure on all governments for democratisation, transparency, and accountability. Social media offers infrastructure to citizen’s initiatives to act, where governments fail, and for governments to work more efficiently with the help of their citizens, may it be on eradicating poverty, fight against corruption, protection of human rights, etc.
With its wide and instant reach, social media is a catalyst of social unrest everywhere where a government is unable or unwilling to listen to its citizens. It can even take down long-lasting authoritarian regimes, as we could see with the incredibly fast spread of Arab spring revolution (starting in Tunisia in December 2010). Victories of perceived underdogs Barack Husein Obama and Donald Trump in US presidential elections in 2008 and 2016 showed us the impact of an organised and targeted campaign on social media can have on political processes in stable democracies as well. In the case of the latter even in total opposition of a vast majority of mainstream media.
Does social media have the power to change the world? (devschooluea)
Newfound space for political influence, however, brings to us substantial risks of political misinformation and abuse in social media as well. We receive crazy amounts of news via social media and it is impossible to reflect on the quality of so much information. All social media is new, so there is little chance to check long term credibility of the source. Such an environment is prone to exposure to misleading and even completely false information – “fake news”, sensationalism and with it populism. With no authority to trust on what is true and what fake, we are inclined to believe the information that is closest to our way of thinking.
In a big chunk of the world freedom of speech is still limited and that counts for social media as well. In China, the state imposed the so-called “Great China Wall”, which does not allow you to seek information on free Tibet, Tiananmen square massacre,… on social media. In many countries (from Turkey to North Korea) any social media is blocked at least from time to time, so the impact of them on societal changes is limited accordingly.
Communication has changed and there is no point denying it. We used to communicate in person. If you needed to communicate with somebody from a different country, you wrote them a mail. It took forever. With digitalisation everything changes. Communication became instant: in merely a second you can spread an information worldwide. How is this possible? Social media is so widespread, that everybody can communicate with everybody all the time. And with a bit more of a 2 billion social media users, sharing information can be almost instant.
See how social media is changing the way we communicate (Zurich Insurance Group)
How does this effect, young people? Since social media become such an important part of young people’s lives, it also influenced their thinking. Before young people were seeking approval in from their peers, but with the wide spread of social media, this need of beeing excepted transferred on the screens. It is getting more and more important to be excepted on social media. And as explained in the next video getting likes it is very important. It gives you a feeling that everybody is paying attention to you and who wouldn’t like that?
How social media is affecting teens (The National)
The problematic part of using social media is from the young age on is that it changes your perception of the world, which in turn change your values and scientists now agree that using social media is changing also your brain. It can be a psychological addiction and it’s users have a hard time turning off. Interesting enough brain scans of these people are showing similar impairment of regions those with drug dependence have. Alarmingly this affects emotional processing, attention, and decision-making. This can be explained since the social media usage provides immediate rewards with a little of medium effort required, your brain begins craving for more and more of those neurological excitement. Interesting it is influencing also your ability of multitasking.
Communication on social medias it is also a bit more self-involved. Compared to 30 – 40% of talk about ourselves while chatting in real life, we spend around 80% of social media communication about our own experiences. Our body is even rewarding us with “dopamine” while talking about ourselves on social media.
5 Crazy Ways Social Media Is Changing Your Brain Right Now (AsapSCIENCE)
The other aspect of how the modern way of life influences our brain is making us more superficial as thinkers. The brain rewards us with dopamine for seeking new information.
For young people seeking information on the internet is a daily activity and this interrupts their focused calm thinking, which is essential for the way we learn. All the interruptions of the digital world (social media, emails, apps) are stopping our memory consilidation. It means transfering information from our short term working memory to our long term memory. And through moving information from working memory to long term memory we create connections and everything else that we know.
What the Internet is Doing to Our Brains (Epipheo)
There is also a phenomenon of The Google effect. With the extended usage of the internet, our brain started to memorize where we find information insted of what is the information. This will happen more and more and is even more visable with young people where a relationship with devices are starthing from the birth. Not remembering pure facts can be in some situation very dangerous (like when a pilot forgets it’s initial training), but on the other hand, FMRI of the brains show, that searching for information online can make our brains more active than reading a book.
Is Google Killing Your Memory? (BrainCraft)
We used to form communities and satisfy our basic needs in local environments. But with the widespread of social media, communities outgrew local environments and become global. Previously we heard that young are joining social media to seek for fame. But that is not it. Young people are driven by two basic needs:
Beeing a part of a community, belonging is one of the most basic human needs. Young people are trying to fulfill it online. They are searching for the right group. Not every group is the one for them. Young people need to be a part of a community. Where they are appreciated, where they feel unique, loved and most importantly where they can be heard. It is important to belong, to feel connected and to be a part of a community.
The second need is a more egocentric one. Online communication allows you to represent yourself in the best possible way. And for young people nowadays it is important to build a superb online personality, where they look better than reality. It is important to build up somebody unique, special and me memorable. Through building up online personas, the process of searching for the meaning of life begins.
Social media sites have tremendous value and potential for learning, socializing, leisure and development of young people. However, they are not always healthy and problem-free environments. Some potential challenges include interference with cognitive processes such as attention, memory, information processing and emotional processing, “Facebook depression”, sexting, exposure to inappropriate content and cyberbullying.
In this chapter, we will be focusing specifically on cyberbullying as one of the most problematic aspects of social media and communication technology. We will be thinking about how having fun online needs to come with responsibility. Social networking can often be just one click away from cyberbullying. The key to decreasing cyberbullying among young people is to ‘think before they click3, especially as just one click has the power to change someone’s life forever.
The first section of this chapter will define key terminology connected to cyberbullying. An overview of what research tells us about cyberbullying and how it works is followed by information on key risk factors and protective factors. Finally, we will list a few guidelines for addressing cyberbullying and legal considerations that we must keep in mind when working in school contexts.
Short definitions below are listed with the purpose of establishing a common language and understanding among stakeholders within our project. They should be considered not final descriptions but working definitions that participants are welcome to discuss, challenge and amend as the project knowledge base evolves.
Bullying is an aggressive behaviour of more powerful individuals against weaker ones, for example hitting, verbally threatening or mocking, spreading rumours, taking the money and other actions. Bullying typically peaks in frequency during adolescence.
Cyberbullying is deliberately using digital media to communicate false, embarrassing, or hostile information about another person. It can happen through cell phones, computers, tablets and other electronic devices and communication tools like websites, text messages, instant messages, e-mail, social networking sites, applications or chat. Cyberbullying is the most common online risk for teens, can occur to any young person online, and can cause psychosocial outcomes4 such as depression, anxiety, severe isolation, and even suicide.
Cyberbullying can have many forms. It can be a mean, hurtful or threatening message to someone or about someone. It can be an embarrassing post, picture or video. It can be a website or a fake profile. It can be a rumour spread by e-mails, texts or posted on social networking sites and many other things. Cyberbullying is often anonymous (the bully does not use his or her name), public (in open view for other people) and viral (rapidly and widely circulates on the internet or through other media). This video can give you an idea how cyberbullying can spread quickly, much like a virus.
Cyberbullying usually includes a bully (or bullies), a target and several observers. Cyberbully is someone who engages in cyberbullying. Cyberbullies use the internet and electronic devices to emotionally hurt others by making fun of them or insulting them.
Targets of cyberbullying are individuals who are hurt by such actions. Most often, cyberbullying does not stay limited to the bully and the target. There may be many observers, who can take on many roles: they can be passive bystanders, they can perpetuate the bullying or they can act to stop cyberbullying.
Cyberbullying is difficult to stop. However, there are things individuals and communities can do to stop it from happening or limit it from spreading. For example, targets of cyberbullying can temporarily limit their online connection time; avoid opening messages from unknown sources, change passwords or accounts. In extreme cases, authorities may get involved and legal actions may be taken.
Often, cyberbullying becomes a bigger problem than just something between individuals. A community might become aware that cyberbullying has become prevalent and threatens the well-being of its members and develop specific measures to fight it and to relieve negative effects. Such activities can be simple activities or complex strategies.
With the rise of cyberbullying, certain organizations, initiatives, and projects have been developed to deal specifically with this phenomenon. Their activities can be online-based (some examples include informational and promotional videos, infographics, websites, virtual campaigns, online courses for teachers and youth workers) or done in-person or through other media (workshops, counselling, lectures, research, training, skill building activities, TV shows or magazines articles). Preventative measures to fight cyberbullying often include basic online safety training.
Online safety or internet safety is a preventative measure. It includes information, knowledge, and skills that help people (including children and youth) be safer while using the internet and online technologies. This includes personal safety, password protection, privacy, security risks and protection from cybercrime in general. You can learn a few simple tips for internet safety for young people in this video.
Digital citizenship is an expression for the norms of appropriate, responsible use of technology.
Digital etiquette or netiquette is a new word that combines the concepts of ‘internet’, networking and etiquette. It means online etiquette, the rules of online communication. Netiquette covers common courtesy online as well as the informal do’s and don’ts of cyberspace.
Respect, educate and protect (REPs) is another popular concept closely connected to digital citizenship that is often used in cyberbullying prevention. It is a way to present nine elements of digital citizenship in a way that is appropriate even for very young learners (from kindergarten level onwards).
Hurting someone’s feelings, causing problems for them and making them feel bad are not new phenomena among young people. We would like to believe that we are teaching young people intra- and interpersonal skills that will help them feel confident in themselves as well as emphatic and respectful towards others, but the reality is that peer bullying has been a big challenge for schools, youth organizations, and local communities for many years. Is cyberbullying just a contemporary expression of this?
Studies are beginning to show3 that cyberbullying is very different from traditional schoolyard bullying. Some important differences are shown in the picture below.
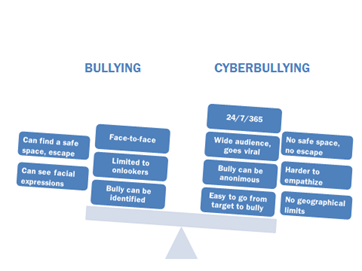
Research indicates that cyberbullying is rarely premeditated like traditional bullying.3 Cyberbullying is often done impulsively and not planned out like in traditional bullying where the bully plans the attacks.
Traditional bullying is usually limited to certain times and places, for example, the playground or the way to school. This gives the target some (although limited) sense of predictability, and there are times and places where he or she can feel safe. In contrast, technology is everywhere: we have our phones and computers around us all the time. Cyberbullying can happen 24 hours a day, 7 days a week and 356 days a year. It can happen in our close proximity or through great distances. It is difficult for the target to find a safe space.
Furthermore, traditional bullying is characterized by the need for power and control, aggression and proactively targeting the target. These characteristics may not be present in cyberbullying cases.
Cyberbullying is “an easier way to bully because unlike traditional bullying it doesn’t involve face to face interaction.”3 Hiding behind the computer decreases empathy the bully feels toward the target. When we do not see the person’s reaction to what we post or text them, we might not know that we have gone too far. Desensitized by the computer screen, it becomes easier to say or do things we would not do to a person’s face. Furthermore, while “traditional” bullies can mostly be identified, it can be very difficult to find out who the anonymous cyberbullies are, making it easier for bullies to avoid seeing and facing the consequences of their actions.
In traditional bullying, we are usually working with a bully, target or bystander. Although we often find that bullies have previously experienced violence themselves (perhaps when they were younger or by someone with more power), the roles in each case are pretty clear. This is not necessarily the case in cyberbullying. Young people often play multiple roles at once, such as cyberbully, target, and witness. There is also no clear-cut profile of who can be the cyberbully and who can be the target, it can happen to anyone.
An especially problematic aspect of cyberbullying is that it often has many, many onlookers. Traditional bullying is more often done in private than in public. But in cyberbullying, technology makes it easy to quickly spread content to a large number of people. Online bullying can quickly become very public or even viral. This wide audience makes the experience especially difficult and embarrassing for the target.
Current research in public health indicates that many “social” factors such as education, socioeconomic conditions, access to services and resources, family ties, employment etc. are closely related to the person’s general health and mental health, including the ability to avoid or cope with violence and “traditional” bullying. Such connections with cyberbullying are less clear. It rather seems that there are no ‘typical’ cyberbullies and targets, it can happen to anyone. For example, it is well documented that in traditional bullying males are more likely to become bullies than females; that older adolescents are more likely to bully than preadolescents, and that bullies are more likely to have low than high self-esteem. For cyberbullying, on the other hand, age, gender or self-perception do not seem to be reliable predictors. Interestingly, high-quality relationships with important adults seem to be a strong protective factor in both types of bullying, traditional and cyber.
Cyberbullying is often done by young people who have increasingly early access to online media and technologies. In this section, we will review how this dynamic typically plays out.
A big part of cyberbullying does not start out with an intention to deeply hurt someone. Young people post or text something they think is a joke or a random comment, but it may not be all that funny for the receiver. In fact, it could easily cross the line to cyberbullying.
In a recent online pilot study, young people who engage in cyberbullying behaviour reported the following reasons for their actions: posting without thinking they could hurt anyone (72%), to get back at someone (58%), the target deserved it (58%), for fun or entertainment (28%), to embarrass the target (21%), to be mean (14%), to show off to friends (11%) and other reasons (16%).
We will be exploring who is especially at-risk of becoming a cyberbully or a target in one of the following sections. For now, it is important to know that cyberbullying can happen to anyone. Relatively little can be said about a typical cyber target or a typical cyberbully: they can be rich kids or poor kids, left-out kids or popular ones, A-students or struggling students, majority or minority students, someone who has been bullied before or someone who has never experienced violence, someone who is online much too much or someone who rarely uses technology, it can be someone who uses technology to pass their free time by browsing and chatting, but also someone who mostly uses it for online learning, research, time management or school.
After the hurtful messages, comments or pictures have been posted recipients are likely to respond inwardly with feelings of fear, sadness, and anxiety. Even if cyberbullying is done jokingly or unintentionally, it does not change the fact that this action can deeply hurt the targeted individual.
Signs that someone is being cyberbullied are similar to signs of being victimized in other ways. Some emotional, academic, social and behavioural indicators to look out for are listed in the chart below12.

Outward responses of cyberbullying recipients can also vary. Some recipients may just ‘shake it off’ and not let it bother them; others may react aggressively or retaliate. Some might respond, but be assertive but polite and others may stay passive and not do anything about the problem. Some might plan steps and actions to take. Some might respond emotionally. They might tell someone or hide what is happening from others or do a range of other things.
In prevention work with young people, it is important to teach them how different kinds of responses are likely to impact the outcome of cyberbullying. For example, retaliation or aggressive response has been shown to make the situation worse, whereas passive avoidance could lead to serious psychological consequences for the targeted individual.
Cyberbullying might die out on its own in time. However, if not stopped, cyberbullying can go on for a long time, and due to its public and viral nature, it can be especially damaging. Prolonged exposure can lead to serious consequences, so it is not advisable to wait. Cyberbullying often stops only through the involvement of outside support, either by contacting the social media used that takes down the offending content and informs the cyberbully of the consequences or through parental and teacher involvement.
Prevention and intervention work for combating cyberbullying should include some simple strategies An example of a useful, simple four-step strategy for dealing with cyberbullying is presented in this video and this worksheet.
After the cyberbullying has stopped, follow-up work needs to be done with targets of cyberbullying as well as the bullies. Targeted young people need support to work through feelings of embarrassment, shame, guilt, fear, isolation, sadness and anxiety. Counselling is often useful.
Cyberbullies, on the other hand, need to be shown the impact of their action and strengthen their social and communication skills, moral reasoning, empathy and conflict resolution skills. Non-judgemental and restorative approaches have been shown effective to stop cyberbullies repeat their behaviour.
What does it mean to be at-risk of cyberbullying? This means that it is quite likely that someone might become involved in cyberbullying; either as a target, as a bully or as a bystander. In the last subchapter, we already mentioned some things that might put someone at risk of or protect them from bullying or cyberbullying.
When we talk about at-risk groups for any problems that children and youth face, we like to think in terms of risk factors and protective factors: what puts someone at risk of unwanted things happening to them? What protects them from the problem or at least from suffering serious consequences? We understand many risk factors and protective factors that influence the physical and mental wellbeing of children and youth, their educational success, their relationships, their self-esteem, their future happiness, job prospects and their resilience to difficult events or other challenges.
For example, we know that children and young people, who face higher risks of becoming involved in ‘traditional’ bullying, often feel lonely, perceive their parents as distant and have problematic relationships with other adults in their lives like their teachers. They might have personal experience with violence in the family, peer group or other immediate environment. Many also have low self-esteem, poor social skills and communication skills. Traditional bullies are more likely to be male than female and more likely to be older adolescents than preadolescents. Targets of ‘traditional’ bullying, on the other hand, are likely to have low self-esteem, distinct physical features are also very common (for example short and weak, glasses, obesity, disability), they are also often less popular among their peers. A very strong protective factor for someone that is a target of traditional bullying, for example, is having a trusted adult that they can talk to about what is happening, or growing up in an environment where information and support are available.
This short sampling of risk factors and protective factors probably seems so self-evident that we do not even need to mention them! However, it is worth mentioning them because something interesting happens when we take a closer look at cyberbullying.
A number of studies and scholarly papers investigate which children and adolescents are most and least at risk of experiencing cyberbullying. Results are interesting and unexpected: when it comes to cyberbullying, there are almost no common risk factors except opportunity. Online access and unsupervised online time and technology use is clearly a ‘prerequisite’ for cyberbullying. However, not all forms of media usages raise the risk of experiencing cyberbullying. Children and adolescents who spend more time using their cell phone are more likely to report receiving aggressive or threatening electronic communication, but no such relationship seems to exist between time spent on the internet and either form of online bullying6.
Most studies find that age and gender do not have a very clear predictive role in cyberbullying. Some early research findings suggested that cyberbullies are often kids who were themselves bullied in real life. But later research found that cyberbullies and targets can just as well be popular, well-adjusted kids who have not been exposed to peer-aggression before. Whereas low self-esteem is usually linked to traditional bullying, many cyberbullies demonstrate a high perception of self-esteem in perceiving their relationships with peers as satisfying. However, feelings of loneliness and a perception of unsafety at school were often linked to cyberbullying.
In short, there seem to be very few common risk factors and even fewer protective factors that would prevent children and young people from becoming involved in cyberbullying. It really can happen to anyone. Research findings suggest that the most important protective factors against cyberbullying are strong parent relationships and positive experiences at school. Restrictions on media use enforced by adults were far less effective in fighting cyberbullying.6
However, although there are few risk factors that can help us predict involvement in cyberbullying and very few protective factors that would prevent children and young people from becoming involved, there are some important protective factors that can help them respond to cyberbullying resiliently. We might not be able to prevent cyberbullying from happening, but we can do things to minimize the damage so that the children and young people do not suffer prolonged or even life-threatening consequences. This can make a key difference in outcomes of cyberbullying both for the bullies and the targets.
Again, strong relationships among children and adults and positive school experiences are the strongest predictors of resilient response for children and adolescents who have faced cyberbullying. More specifically, students tended to behave resiliently if they:
Children and young people who have been onlookers are often at risk of perpetuating such behaviour. This is why it is so important to build healthy, empowering communities where cyberbullying does not go unrecognized, where such behaviour is talked about and challenged and where solutions for better relationships are found and invested in.
Cyberbullying has many forms and can include a variety of acts. It can be sending a mean text message, making online threats, sending unwanted provocative photos, posting insults or hate speech, attempting to infect the target’s computer with a virus, flooding an e-mail inbox with messages2 or sending harmful material and any other form of social aggression using the Internet or other digital technologies. Some of the most common cyberbullying tactics are briefly described below.
Cyberstalking: a bully repeatedly and intensively harasses, denigrates or threatens the target, enough to create fear.
Cyberthreats: a bully makes threatening remarks on the internet or implies violent behaviour. It can also be threatening with suicide.
Denigration: a bully starts rumours about a person to damage their reputation. “Dissing” someone online.
Exclusion: a group of bullies excludes someone from online conversations, groups or from events shared online to hurt their feelings.
Flaming: a bully starts or fuels online fights exchanged through emails, instant messages, chat rooms or comments. There is often harsh language directed towards a specific person.
Harassment: a bully repeatedly sends or posts mean, hurtful or insulting messages or comments.
Masquerading/impersonation: a bully creates a fake identity to harass someone anonymously or impersonating somebody else to him send malicious messages or post material to get that person in trouble or danger or to damage that person’s reputation or friendships.
Outing: a bully shares someone’s secrets or embarrassing photos online.
Trickery: a bully tricks someone to share private information or photos with them and then shares this online.
Of course, this is just one way of classifying cyberbullying. You might find another model that helps you and the young people you are working with even better. But it is always useful to have some language and tools to think and talk about a problem. Take a look at some real life examples below and think about them. Can you identify types of cyberbullying in the following examples? What would you do if you came across one of these messages in real life? How could you talk to a sender of these messages? How could you talk to the recipient?
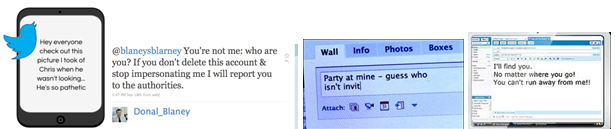
 |
Source: |
Educators, youth workers, parents and other adults working with children and young people are likely to come across cyberbullying incidents. To successfully deal with cyberbullying we must first learn to recognize it, analyse it and understand what exactly is going on. Secondly, we need to be aware of effective strategies to support the victim and challenge the bullying behaviour.
Our reactions will often determine the outcomes of cyberbullying incidents: what will be the consequences for the victim, the bully, and the onlookers; how will the community and relationships be shaped by this experience; will children and young people learn from it or be harmed by it? Furthermore, when faced with cyberbullying cases we might want to think about how to prevent similar events in the future and how to help children and young people develop skills for healthy, positive use of online media and communication technology.
In the following section, we have compiled short descriptions of six real-life cyberbullying cases that are also available on the internet in even more detail. We would suggest you take the time to read through them, think about them and try to propose solutions or guidelines for intervention. For the first three cases, we have already outlined some bullet points to help you think through them. However, these are suggestions rather than definite solutions. You might find solutions that are even more appropriate for your school, your community, your group of children or young people.
Case studies are a helpful tool to practice and apply concepts and skills that we have learned in Chapter 3 of this manual.
To facilitate a training session using case studies, you might follow these steps:
Case studies are also a very helpful tool to work with children and young people. Real cases and specific situations are something they can understand and relate to. Experience helps them learn. You can use case studies during cyberbullying awareness workshops, mediation club meetings and in conflict-resolution training sessions. You might want to have the students read and discuss the cases or even use role-play to act them out.
However, a word of caution: students might perceive these cases very differently than adults. Make sure the case descriptions are age-appropriate, understandable, short and concise. A very important point is also NOT to overburden students emotionally: for example, it might be very difficult for them to process stories about cyberbullying resulting in suicides of young people. We also strongly encourage you to use case studies with happy or open endings when working with students.
 Ashley lives in Colorado and has been growing up like any other teen, being influenced by her peers as much as she’s influenced by her parents’ guidance. However, she never expected how invasive the Internet could be without her knowing about it or even having a say in the matter. In Ashley’s case, the bullying that occurred may seem benign on the surface, but it had the potential to be far more.
Ashley lives in Colorado and has been growing up like any other teen, being influenced by her peers as much as she’s influenced by her parents’ guidance. However, she never expected how invasive the Internet could be without her knowing about it or even having a say in the matter. In Ashley’s case, the bullying that occurred may seem benign on the surface, but it had the potential to be far more.
Unknown to Ashley at the time, a classmate when she was 11 began taking photos of her. The images were then made part of a portfolio of information posted on the Internet with a fake social media page. The topic was Ashley and the website page was made to look as if Ashley posted everything herself. It was only through friends and third parties that Ashley became aware of the existence of the online information. The data was detailed as well; it included her school name, her home address, her family information, birthdays and more. Worse, all the data was set to be wide open to the public without any filtering or restriction. The creator of the page was confronted but denied the act. In the meantime, Ashley began to be ostracized by her friends at school. To break the freeze-out cycle Ashley had to enrol in a different middle school to regain a “clean slate.”
In Ashley’s case, the damage was limited and constrained to the loss of a few friends. However, it could have been far worse. Further, the damage was caused by another child who simply had the time and access to post whatever was desired on the Internet for anyone to read.
 |
Source: |
 |
Type of cyberbullying:
Masquerading (creating a fake identity or impersonating someone) |
 |
The (we try to avoid an ascription like typical because anyone can be affected) victim profile:
Could be anyone. Likely to be an outsider |
 |
The cyberbully profile:
Could be anyone. Likely does it for fun or out of revenge. |
 |
How to promote constructive use:
|
 |
How to prevent it from happening:
|
 |
How to react if it happens:
|
 Jessica Logan was an 18-year-old high school senior who sent nude photos of herself to her boyfriend. After the couple broke up the boyfriend sent the photo that was meant for his eyes only to hundreds of other teenagers via group chats. The photo sharing led to name calling and taunts at school. Phrases like “slut, porn queen, and whore” were regularly spoken referring to Jessica by schoolmates. The taunting continued via Facebook and through text messages.
Jessica Logan was an 18-year-old high school senior who sent nude photos of herself to her boyfriend. After the couple broke up the boyfriend sent the photo that was meant for his eyes only to hundreds of other teenagers via group chats. The photo sharing led to name calling and taunts at school. Phrases like “slut, porn queen, and whore” were regularly spoken referring to Jessica by schoolmates. The taunting continued via Facebook and through text messages.
Jessica was feeling miserable and depressed. She was afraid to go to school and started skipping classes. Jessica’s mother only learned of a problem at all when she started getting letters from school reporting that her daughter was skipping school. Jessica’s mother took away her daughter’s car and drove her to school herself, but Jessica still skipped classes. She told her mother there were pictures involved and a group of younger girls had received them and were harassing her and calling her vicious names. Unfortunately, the mother didn’t realize the full extent of her daughter’s despair.
When the school officials became aware of the harassment they offered to go to one of the girls who had the pictures and tell her to delete them from her phone and never speak to Jessica again. Jessica’s mother saw the solution in talking to the parents of the girls who were bullying Jessica, but her daughter said that would only open her to even more ridicule.
2 months later Jessica committed suicide.
 |
Source: |
 |
Type of cyberbullying:
Outing (sharing someone’s secrets or embarrassing photos online). |
 |
The victim profile:
|
 |
The cyberbully profile:
|
 |
How to promote constructive use:
|
 |
How to prevent it from happening:
|
 |
How to react if it happens:
|
 At the beginning of the school year, Sara moved into a new school. At first, things were great and Sara was very popular. However, after a couple weeks at her new school, her parents noticed that she seems depressed and anti-social. They observe that she rarely socializes with her friends. Sara’s parents are worried about her and suspect that something is not quite right at school. They try to talk to Sara, but she is reluctant to talk. She tells them that she and her friends had an argument and are not getting along. Sara’s parents do not realize the problem is more dangerous than a disagreement between friends.
At the beginning of the school year, Sara moved into a new school. At first, things were great and Sara was very popular. However, after a couple weeks at her new school, her parents noticed that she seems depressed and anti-social. They observe that she rarely socializes with her friends. Sara’s parents are worried about her and suspect that something is not quite right at school. They try to talk to Sara, but she is reluctant to talk. She tells them that she and her friends had an argument and are not getting along. Sara’s parents do not realize the problem is more dangerous than a disagreement between friends.
One day as Sara arrived at school, other students began to giggle and laugh at her. Some even made strange remarks about her eating lunch in the lunchroom. Sara was embarrassed and confused. She did not mention this to anyone that day and thought that it would just go away.
After returning home from school, Sara decided to check her email. She had one email from a person that she did not recognize. Inside the email, was an embarrassing picture of Sara in the lunchroom eating. Immediately, Sara realized that this picture was the reason that all the students had been laughing at her when she arrived at school that day. Another student must have taken this picture in the lunchroom at school and sent it to everyone in her class. Sara was alarmed and began to cry. She immediately deleted the email and did not tell anyone about the email.
As the weeks passed, the incidents escalated. Sara received more and more embarrassing and sometimes even threatening emails from the person. She deleted each and every one. Sara was too humiliated to tell her parents or her teachers. Her teachers noticed that she had begun to fall behind in school and seemed to be very depressed.
 |
Source: |
 |
Type of cyberbullying:
Outing & Harassment (sending or posting nasty, mean, embarrassing messages). |
 |
The (we try to avoid an ascription like typical because anyone can be affected) victim profile:
Likely to be an outsider (new kid, shy, different…), but could be anyone. |
 |
The cyberbully profile:
|
 |
How to promote constructive use:
|
 |
How to prevent it from happening:
|
 |
How to react if it happens:
|
 Gina, an exuberant and spirited high school freshman, had a falling out with a girlfriend over a boy they both liked at school. It wasn’t long before Gina began getting rude text messages to her phone at all hours, calling her names and saying inappropriate things such as, “I hope you die soon.” The angry friend had enlisted others to text hateful remarks to Gina too.
Gina, an exuberant and spirited high school freshman, had a falling out with a girlfriend over a boy they both liked at school. It wasn’t long before Gina began getting rude text messages to her phone at all hours, calling her names and saying inappropriate things such as, “I hope you die soon.” The angry friend had enlisted others to text hateful remarks to Gina too.
Gina’s parents had never talked to her about bullying, or how to handle such behaviour when you become the victim. The 14-year-old was completely unprepared to face such a major assault on her self-esteem. She was devastated, and soon began to withdraw from her friends and active social life. She spent more and more time alone in her room. Her mom grew concerned when Gina would no longer talk about what was going on at school or in her life. So she reached out to one of Gina’s closest friends and learned about the hateful texts her daughter was receiving.
Gina’s mom took action before the emotional toll became worse. She told Gina she knew about the cyberbullying, and together, they discussed the situation with the school counsellor and principal. With support from her family and teachers she trusted, Gina found the strength to talk to the girlfriend she had argued with, apologized for the quarrel and asked her to call off the texting campaign. While their friendship was over, the cyberbullying stopped.
 |
Source: |
 Ryan Halligan was a 13-year-old middle schooler from Vermont who first experienced bullying in the fifth grade because of his poor physical condition. By the time he made it to seventh grade Ryan was begging his parents to home school him or if they could move. His parents contacted the school and tried to work out the issues. Boys at school started rumours that he was gay. Over the summer he worked on establishing a relationship with a popular girl from his school online. When he returned for his eighth grade year, and went to approach his girlfriend in real life, where she told him in front of all her friends he was a loser and that everything she had said to him online was a lie. The girl had copy/pasted all of their instant messages and sent them to a friend for a laugh at Ryan’s expense. Humiliated, Ryan took his life.
Ryan Halligan was a 13-year-old middle schooler from Vermont who first experienced bullying in the fifth grade because of his poor physical condition. By the time he made it to seventh grade Ryan was begging his parents to home school him or if they could move. His parents contacted the school and tried to work out the issues. Boys at school started rumours that he was gay. Over the summer he worked on establishing a relationship with a popular girl from his school online. When he returned for his eighth grade year, and went to approach his girlfriend in real life, where she told him in front of all her friends he was a loser and that everything she had said to him online was a lie. The girl had copy/pasted all of their instant messages and sent them to a friend for a laugh at Ryan’s expense. Humiliated, Ryan took his life.
 |
Source: |
 Henry was a shy sixth-grader who recently arrived at school from out of state. One day as he was browsing a social media site he came across a page about the school with pictures of students, including one of him labelled “The Fat Nerd.” Upset, he posted a reply expressing his dismay.
Henry was a shy sixth-grader who recently arrived at school from out of state. One day as he was browsing a social media site he came across a page about the school with pictures of students, including one of him labelled “The Fat Nerd.” Upset, he posted a reply expressing his dismay.
The postings became nastier, and soon some students were making loud comments in the lunchroom and on the playground. Henry had to endure many weeks of feeling humiliated and hurt before anyone realized what was going on. His parents didn’t even know because Henry was too embarrassed to tell them. Finally, a teacher overheard some of the names and asked Henry what was going on. He described the social media page and cyberbullying.
The school, which had trained its teachers and had a zero-tolerance policy on bullying, responded quickly. They identified the ringleaders, and with the help of their parents, had the creator of the unauthorized school page take it down from the social media site. School officials hosted sessions for parents and students about cyberbullying and how to prevent it.
 |
Source: |
As we learn more about cyberbullying, the question inevitably arises:
This section of the manual is designed as an overview of guidelines, ideas and resources on how to tackle cyberbullying. Guidelines can provide a useful framework for all concerned to reduce cyberbullying and its negative effects1, but of course they need to be followed by practical and effective action plans.
We will be focusing specifically on guidelines and suggestions for school environments. Throughout the world, school environments are (apart from online environments) the most utilized platforms for cyberbullying prevention and intervention.
During 2008-2012, an interesting international study was done in 29 (mostly European) countries, including Germany, Slovenia, Poland, Italy and Hungary1. In addition to a comprehensive review of available literature and research on cyberbullying, one of the project objectives was to analyse existing nationally published guidelines connected to technology use and cyberbullying from different countries. The aim was to disseminate best practices and to develop a set of common guidelines applicable on the European level.
Researchers reviewed 54 national guidelines (two per country) and scored each document on a number of criteria. They found that the most common target groups were parents (addressed in 41 documents), young people (35 documents), teachers (32 documents) and schools (23 documents). The key findings were that the existing guidelines varied greatly in covering important aspects of cyberbullying. Many documents emphasized skill building, awareness raising and modelling appropriate behaviour. School policies were often mentioned but not elaborated on.
Based on this comprehensive analysis, a number of recommendations were made for each target group. The following subchapters will summarize the recommended guidelines1 blended with some ideas and resources for further exploration. Guidelines are divided in four sections that are important for designing a good school-wide strategy:
In each section, suggestions are given for each of the main identified stakeholders: young people, parents, teachers, and schools.
Firstly, guidelines for raising awareness about cyberbullying and skill building are presented for all stakeholders. This is the strongest area of many anti-bullying programs, including typical school strategies.
 |
Young people need:
|
 |
Parents need:
|
 |
Teachers need:
|
 |
Schools need:
|
A good school-wide approach against cyberbullying includes proactive school policies, plans, and procedures that are effectively implemented in practice and regularly evaluated. The following guidelines emphasize some relevant considerations from the viewpoint of different stakeholders.
Firstly, guidelines for raising awareness about cyberbullying and skill building are presented for all stakeholders. This is the strongest area of many anti-bullying programs, including typical school strategies.
 |
Young people need:
|
 |
Parents need:
|
 |
Teachers need:
|
 |
Schools need:
|
Schools and families are among the most important risk factors as well as protective factors in cyberbullying. To deal with cyberbullying effectively, links between communities need to be established and resources in local communities should be utilized. The following guidelines discuss the needs of all stakeholders from the partnership building perspective.
 |
Young people need:
|
 |
Parents need:
|
 |
Teachers need:
|
 |
Schools need:
|
The ‘climate’ or rather the ‘culture’ of social environments that students are a part of, plays an often invisible but important role in cyberbullying prevention and intervention. The following guidelines examine what different stakeholders need to contribute to a positive, healthy, bully-free social environment.
 |
Young people need:
|
 |
Parents need:
|
 |
Teachers need:
|
 |
Schools need:
|
Cyberbullying is a real problem and it happens more often than we know or expect. Schools sometimes became aware of the problem but are poorly equipped to handle it. School staff might not know how to respond, what their competencies are and what is out of their area of expertise, how to respond to one-time incidents or how to develop a school-wide strategy if cyberbullying has escalated. Teacher and other school staff members often report that they would like to react, but do not know how and they feel powerless.
In this section, we will explore some basic guidelines and strategies for schools that wish to address specific cases of cyberbullying among students.
Cyberbullying is only one form of unacceptable behaviour that we might encounter among students. Schools often do not have a strategy or a procedure to deal specifically with cyberbullying; however, most schools have codes of conduct, policies for dealing with unacceptable behaviour or even counter-bullying policies. Cyberbullying should be dealt in the context of these policies.
Staff members usually become aware of cyberbullying through student reports, parent reports or by noticing problematic online activities or changes in student behavior.
The cyberbullying incident may take many forms and need different approaches. The first step is to think about the incident. Some of the key questions are:
Each case of suspected or alleged cyberbullying should receive an immediate response. If needed, a wider strategy should also be implemented.
If staff member suspects or is told about a possible cyberbullying incident, there are some steps they can take to immediately respond to the incident.
 |
Cyberbullying over mobile phones:
|
 |
Cyberbullying on computers:
|
Students that are victims of cyberbullying may need different types of support:
Offer students what you can and help them find support in areas you are not able to help them. School counsellors are usually key staff members for organizing a support strategy and support network for the student.
The nature of investigation will depend on each specific case of cyberbullying. It might include:
Take note that in most European countries, school staff members do not have the authority to search students’ belongings, including their phones, tablets, and other devices. You may ask the students to show you the devices and the content, but you cannot make them do it.
If the incident has signs of a criminal offense, the school is mandated to report to authorities and should be careful not to interfere with police investigations.
Working with the cyberbully or bullies is just as important as working with the victims. The consequences should be determined on an individual basis and should be in accordance with the rules and procedures the school has in place. Working with the bully should have the intention to:
A strategic approach to cyberbullying is not always needed. Usually, a general strategy to ensure a good school climate, a strategy to develop students’ social skills and/or a conflict resolution strategy might be enough to prevent most cases or at least the most serious cases of cyberbullying.
If the school detects one isolated incident of cyberbullying, it should deal with that specific incident, but it might not make sense for a school-wide strategic approach. However, if there are many incidents or if their impact is potentially harmful, the school should review its existing policies and if needed, develop new ones.
Some of the tools that the school might use are:
The following case studies can be used as an exercise to help you think about common scenarios, connected to cyberbullying, that might happen in schools. In each case, a cyberbullying incident is summarized and a brief description of a context is given. Think or talk about how you might respond to such cases. Try to plan an immediate response as well as a school-wide strategic intervention if it is needed.
 School context: High school in an urban setting, in the city centre. The student population is very diverse: some students come from middle-class families, some from a poor background and a few from wealthy families. The school has about a third of minority students. The school general climate is pleasant, students tend to like school and most of them have a group of friends in the school. Students often approach teachers with their problems. There have not been many cases of cyberbullying reported yet and very few cases of traditional bullying. The school has an anti-bullying policy and monthly bullying prevention assemblies for students.
School context: High school in an urban setting, in the city centre. The student population is very diverse: some students come from middle-class families, some from a poor background and a few from wealthy families. The school has about a third of minority students. The school general climate is pleasant, students tend to like school and most of them have a group of friends in the school. Students often approach teachers with their problems. There have not been many cases of cyberbullying reported yet and very few cases of traditional bullying. The school has an anti-bullying policy and monthly bullying prevention assemblies for students.
Case summary: Sara, age 14, has reported being cyberbullied to the school counsellor. She had sent some ‘dirty’ photos to her 15-year-old boyfriend through Snapchat. He has shown the photos to his friends and now the boys are making fun of her. They are calling her names as she walks by them in the hallway. She has also received 13 Snapchat messages requesting naked pictures of her. The principal and the teachers have not reacted yet but plan to discuss the incident during the teachers’ conference next month. None of the other students have been approached about the incident so far.
Initial investigation: When Sara reported the incident, the school counsellor took notes of her statement. Since Snapchat deletes shared content after it has been viewed, no record of either the photo or the messages exists.
In general, students in the school are very skilled in using social media. Almost everyone has a cell phone and most of the students use Facebook, Instagram, Twitter, Snapchat, Viber and Whatsapp. They use social media for fun, to send photos, videos, to express themselves. Teachers are mostly familiar with social media platforms, more than half of them also have Facebook, Twitter and Instagram profile, some are also using Whatsapp.
 School context: High school in a small town. Most students come from upper middle class families and live in suburban areas. The local communities are close-knit, most students, parents and teachers know each other by name.
School context: High school in a small town. Most students come from upper middle class families and live in suburban areas. The local communities are close-knit, most students, parents and teachers know each other by name.
Case summary: One case of cyber bullying has happened so far: exclusion of a boy Tom, age 15. His peers were calling him names and making fun of him through Facebook. Tom was also bullied in person: two boys hit him in the stomach and threatened to do it again if he told anyone. One of the teachers has seen that incident (in person) and after asking the boy, Tom told her that he was also bullied through social media, mainly Facebook. After that, the homeroom teachers talked with the bullies: three older students aged 18. They denied that they did anything bad or wrong; they didn’t see it as hurtful, just as innocent jokes. They promised not to do it again.
Initial investigation: After this incident, teachers wanted to know more about how students use social media. One of the teachers mentored a student research group which wrote a research paper on the topic: they did a survey among all students and found that students know and love to use social media, mainly Facebook, Instagram, Twitter, Snapchat, Viber, and Whatsapp. They use the applications and platforms to stay in touch with friends abroad or from other cities, to talk in groups, to send photos and videos to each other. Teachers mainly use and know only Facebook, less than half of teachers have their own profile social media sites.
 School context: Primary school in an urban setting.
School context: Primary school in an urban setting.
Case summary: Tina (age 10) mentioned during one of her random conversation with her teacher that some unknown ‘boy’ was inviting her to meet up with him. They started talking through Facebook (he ‘added her as a friend’ and she responded, even though she does not know him in person). At first, he was nice and friendly, but after some time he started asking her to send him photos of her and pushing her to meet up in person. The teacher asked if her parents know and she said that “Of course not”, they don’t talk about that at home, her parents do not know/use social media, and therefore they cannot understand the situation. She does not think of the situation as problematic, she is just a little bit annoyed with that boy and not sure if she wants to meet up with him in real life.
Initial investigation: Social media and technology is popular in the school. Some teachers are very fond of Social media and use it daily. One of the teachers (Geography professor) made a survey and realized that more than 80 % of students are using social media. They use mostly FB, Instagram, Whatsapp, Snapchat. Teachers also started an official FB and Twitter profile of the school one year ago and are posting interesting photos, motivational quotes, videos, events on the wall. The profiles have cca. 500 followers. Most students have computers or tablets at home, about half of them have cell phones. Most students know about Social media and apps like Snapchat, Viber, Whatsapp, and about half of the students use them and have social media profiles. Teachers and students are “friends” on social media.
Several countries across the globe have already developed seemingly effective cyberbullying laws. The strictest cyberbullying laws in the world are reported to be those found in Canada where under the Education Act individuals who engage in cyberbullying face suspension from school, and repeat offenders may also face expulsion from school and possible jail time. In United Kingdom, cyberbullying could result in six months or more in prison and a fine under the Malicious Communications Act. Certain states of the USA are also considered to have strict legislation with legal consequences ranging from monetary fines, charges of misdemeanour or imprisonment; whereas other US states have looser or no specific cyberbullying laws. Effective legislature is also reported to be in place in the Philippines and Australia.2
In Europe, most countries do not have specific cyberbullying laws, but there are a number of existing laws that can be applied in cases of cyberbullying. Some countries have specific measures for certain online behaviours (for example, cyber stalking is illegal in Poland). International law covers some of the problematic areas: Convention on Cybercrime and European Data Protection Legislation is now being applied to issues of cyberbullying, online harassment and identity theft.
Cyberbullying is a relatively new phenomenon. A need for anti-cyberbullying legislation is being recognized in many countries as cyberbullying can have serious consequences for individuals and communities. Many countries are beginning to recognize the emotional and physical harm that can result from cyberbullying and are designing protective measures and policies.2
Most legal definitions describe cyberbullying as:
Because the use of mobile and online communications has grown so rapidly and the crime is relatively new, many jurisdictions are deliberating over cyberbullying laws. However, if an online activity has indications or elements of a criminal act, existing laws should be considered, for example criminal law (assault, threats, harassment, protection of minors), civil law (defamation, data protection, consent), and in some cases regulations in special areas are also applicable (education, family, employment, human rights, data protection).
Cyberbullying is a serious problem and potentially extremely harmful. But in fact, a very small part of cyberbullying can be considered illegal activity. Most such behaviours are unacceptable behaviours that can and should be dealt with in the context of family and school environments.
However, at times cyberbullying incidents can have signs of criminal activity. We might believe there is a real threat to the target or the line toward harassment can be crossed. In such cases, local police departments or attorneys can be consulted to determine if the case should be reported to authorities.
It is important to realize that even if cyberbullying behaviours are not considered criminal acts, civil lawsuits may still be filed to determine the damage resulting from cyberbullying.
When designing policies and actions to fight cyberbullying, the applicable legislature should be considered. Specifically, school staff, youth workers, and parents should be aware which actions need to be reported to authorities.
In some cyberbullying cases, it may be advisable to inform the local police department or consult an attorney. Very few cases of cyberbullying are being reported to the police, and even fewer are found to have characteristics of criminal acts and are investigated, eve fewer are persecuted. However, it might be better to err on the side of caution.
In most European countries, professionals working with children are required to report to authorities if they suspect a child is being abused, in danger or if there is a criminal act being planned. This is called ‘mandated reporting’. Often, schools and organizations have procedures and rules in place for such situations. It is advisable to review such rules and consider how they might be applicable to cyberbullying.
It might be difficult to assess if an incident or behaviour needs to be reported to authorities, especially in the context of cyberbullying. Some questions to consider are: Was the child physically or psychologically harmed in the incident? Does the incident pose a future threat to the wellbeing of the child? Would a reasonable, impartial person believe that there is a serious threat? Is there anyone that can be consulted? Often police officers specializing in child protection or cyber-crime are happy to help you discern if the case should be reported, or a national agency dealing with cyber safety might be able to provide some insight.
Lack of awareness about reporting cyberbullying can be detected in many settings. For example, a study of national-level guidelines for cyberbullying prevention and intervention in 27 European countries1 found that whereas the importance of maintaining privacy and the need for reporting procedures were mentioned in around 50% of the guidelines, only about one-third included references to reporting incidents to the Police.
Even though not all cases of cyberbullying can be considered criminal acts and although not every case needs to be reported to the police, cyberbullying should be reported to the platforms used to carry out the abuse.
Most social media providers have clear rules and terms of use deeming cyberbullying as unacceptable and a violation of terms of use. Most social media also have easy, anonymous reporting systems. For most social networking sites, the general reporting address is: [email protected]
Social media tend to take reports of cyberbullying and other forms of online abuse very seriously. In most cases, the site will take down the offending content and sometimes ban the bully from using the site. They also have resources to track activities, restore deleted content and identify the bully, although this information might not be available unless specifically requested by authorities.
The key step is to teach young people to be aware that social media they use have rules about acceptable online behaviour and terms of use that need to be followed. Not complying with these rules can have consequences. Cyberbullying is not acceptable online behaviour, and if they see it, they should report it right away. The site will take down the content and they can feel good knowing that they took assertive action to help stop cyberbullying.
In previous chapters, we encountered how young people live their lives merged with social media and which are the posing risks of this kind of a lifestyle. We presented cyberbullying and recommendation for lessening its effects in the school environment.
In the project Joining Forces to Combat Cyberbullying in Schools, we tested different approaches of to tackling cyberbullying and compared them with conclusions and researches of previously implemented projects. Based on our conclusions we believe that we can only stop cyberbullying with a holistic approach that entitles:
This approach addresses three target groups whose behaviour affects at most the occurrence of cyberbullying in the school environment:
This chapter represents the core of this publication. Interlinking knowledge about cyberbullying, youth and social networks (more detailed presentations can be found in previous chapters) with concrete measures and guidelines for implementation (which are presented in next chapters).
The World we live in consists of different subsystems. Each individual has certain genetic predispositions, lives in a specific family and grows up in a unique local environment with all its specifics. He attends school with a specific subculture, becomes friend with certain people and with them develops specific activities. His behaviour and attitude towards cyberbullying can be influenced by all of those predispositions. Some have more effect and others less, some can have a bad, others a good influence and the amount and connotation can differ from a person to person. It is not enough to change individual attitude and behaviour (we can do that with education,…). For an efficient change, we need to address everything around him, all categories and subsystems.
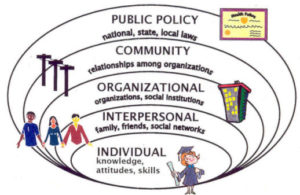
Source: http://www.balancedweightmanagement.com/Socio-Ecological%20Model.jpg
Socio-ecological model recognises various levels of addressing social problems: individual, interpersonal, organisational, community, and public policy.
Approaches on different levels require specific unique unalike strategies. As with all others issue it is usually easier to tackle them on lower levels (individual, interpersonal) and most cyberbullying prevention project is presenting educational workshops and raising youth awareness as their main outcome. Addressing the higher levels can require more sources, more time and a higher level of professionalisation.
A set of actions presented in this manual is primarily focusing on the organisational level.
Addressing these levels automatical includes tackling all the lower levels as well, individual and interpersonal.
We chose organisational level because it:
The project has certain effects also on the community level (cooperation project partners and schools in the coalition, creating a joint knowledge) and on a public policy level (action proposals).
The project has certain effects also on the community level (cooperation project partners and schools in a coalition, creating a joint knowledge) and on a public policy level (action proposals).
The aim of Joining Forces to Combat Cyberbullying in Schools project was
To change school cultures towards bullying-free zones through addressing the challenge of cyberbullying from different angles and through the combination of different actions.
During the implementation of pilot activities in the project, several principles stood out, that would apparently be important when addressing the challenge of cyberbullying in schools.
Following these principles, 4 measures have been developed and tested. Together, they form a system of measures prepared to implement in a specific school culture.
Each of individual measures focuses on more fields like promotion, prevention and intervention. But each acts primarily just on one.
| Promotion | Prevention | Intervention | |
| Awareness raising | X | ||
| Mediation Clubs | X | ||
| No blame approach | X | ||
| Creativity Groups | X |
As an actor in the school environment with its specifics needs and challenges, you can focus on one, two, three or all four of proposed measures. The decision is yours. In the frames of project, we also implemented two additional measures, that can help you:
| TG1: Parents | TG2: School staff | |
| Aim 1: the phenomena of Cyber Bullying and its consequences. | There is bullying going on in social media. Some teenagers suffer. Probably your kid was already part of cyberbullying – in one way or another. | Bullying and cyberbullying exist in nearly every classroom. If it escalates, you could have many problems. Prevention is a key to success. |
| Aim 2: proper use of Social Media | Your teenagers are well equipped with technical skills but they lack social skills on social media! | Learning to use social media is not only about technical skills. It is also about social skills. |
| Aim 3: possible strategies to combat Cyber Bullying. | Pay attention to symptoms of possible cyber bullying. Symptoms are … | There are many ways to address cyberbullying in schools: promotion, prevention, intervention. |
| Aim 4: possibilities this project will offer them in the future. | Your kid could visit a summer camp about cyberbullying, he/she could also attend some mediation courses and obtain these skills. | You can get trained in NBA skills. You can facilitate a mediation club in school / become a mediator yourself or train peer mediators. |
Based on school testing in schools within the project “Joining Forces to Combat Cyber Bullying in Schools”, we are suggesting a holistic combined approach which we presented in the fifth chapter. It consists of four activities: Awareness Raising, No Blame Approach, Mediation Clubs and Creativity Groups.
And in this chapter, we will introduce you to our first activity: Awareness Raising. It is focusing on three target groups that are most involved in cases of cyberbullying in the school environment: student, school staff, and parents.
We are presenting two implementation plans of awareness raising with students – one that takes half to one working day and the other that can be implemented in a short workshop. We also prepared a program for school staff and another one for parents and at the end you can find suggestions for additional activities, that you can use if needed.
The time of awareness raising activities will probably be short and the number of participants high. However, it is strongly suggested to find ways to interact and start a dialogue with the audience in order to engage them in the lesson and especially push them to come out with their own idea before we explain our point of view.
We recommend the use of some short videos to break the flow of the lesson and keep their attention on a high level. Some suggestions include:
 |
Duration:
4-5 hours |
| Program | Time | Material |
| Warm welcome, presentation of the trainer team, objective of the activity, presentation of the students | Up to 30 min | circle of chairs, flipchart, moderation material – should be organized beforehand! |
| Expectations of the day of the participants
Division into groups up to 4, 5 min discussion, group chooses 5 expectations and visualizes them on cards (per card only one expectation), Groups share their results – team wraps up |
15 min | cards, markers, scotch, pin board |
| Overview of media usage and equipment Oral exchange in a big circle:
|
10 min | circle – plenary |
Exchange of the danger of using the net – “to carve out” the disadvantages – group work:
Each group writes the experiences on a flipchart as a list or mind map and presents it |
30 min |
markers and flipchart paper
|
| Break | 15 min | |
| Transfer of perspectives – opinion barometer
Group will listen to statements and every individual decides which position reflects his/her personal opinion – the team will ask some students representing different positions for their reasons – the other students only listen – no discussion After some statements and listening to arguments, the students will take their seats again and the team will raise open questions:
|
30 min | Prepared statements line with comments |
| Verbalisation of a definition of cyber-bullying by listening to a little story – presented by the team
Plenary: what does cyberbullying mean? Brainstorming and the team will pick the main elements to formulate the definition with the agreement of the students |
15 min | Flipchart and the story in your country language |
Deepening of knowledge of different perspectives:
Students take turns to slip again into the different roles. The team doesn´t comment at this point. Students who approach Kim´s card will be asked: ” Why is Kim doing this, what do you think?” The question to the bystander role: “ Why do they join in, what could be their motivation?” Question for the observers: “What hindered the observers to intervene in favor of Joe? Summary of the team, students are asked to let go of the roles. |
20min
25min |
Internet-connection , beamerRole cards with the name of the actors of the videoclip |
| Long break
|
30-60 min | |
| Energizer | 10 min | |
| Development of strategies to react in situations of cyberbullying and prevention – students will be divided into two-three groups, parallel group work sessions and presentation – the other group can add ideas and propositions. | 30min | |
| Evaluation and feedback. How was the day – looking back to the expectations and giving space to express impressions and feelings? In addition, students could be asked to write a letter to themselves where they reflect how they will react in the future in case of cyberbullying. Letters will be collected by the team and send to them later by post.
The team will cordially thank the students for their participation and input. |
20 min | Feedback questionnaires if wanted |
A follow-up session after 2-3 weeks would be appreciated to enhance the motivation to fight cyberbullying.
Possible questions:
 |
Duration:
90 minutes |
 |
Aim:
|
| Program | Time | Details |
| The project | 10 min | What is this European project about? Which other countries are working together with us? |
| Introduction: what is the Internet? | 15 min | Question and interaction to warm up:
(What is the “Internet”? When was the Internet born? How can the information “run” to the other part of the world in less than a second?…)
(What are the best use and the worse?) Conclusion and message: The Internet is not virtual at all… it is the biggest communication network ever existed, based on a huge number of infrastructures (servers, fiber-optic cables, ocean cables, antennas…) and services companies with thousands of employees and billions of real people connected to it. Good or bad? It can be both very good and very bad… it’s up to us, and the way we choose to use it. We all are responsible for making it a better and useful place. |
| Overview of the main “web-safety” issues | 20 min | Question to kids
Presentation (each topic may be associated with a catchy image and a keyword)
Conclusion with interaction and message:
(because we don’t know the consequences because we feel smarter because we follow the “crowd”, or the fashion of the moment, lack of EMPATHY…) |
| Cyberbullying | 20 min | Presentation of the topic
Conclusion and message: Cyber-bullying is not a game. It can happen to anyone. Everyone is responsible for stopping / reporting it to reduce the damages. Empathy is a key point: if we put ourselves in the victims´ shoes than we can understand there is no excuse not to act against it. |
| Conclusions | 15 min | What we can do together:
(suggest not to mention NBA approach in this context since this is more useful for Teachers and Parents)
|
| Conclusions | 10 min |
|
 |
Duration:
90 minutes |
 |
Aim:
|
| Program | Time | Details |
| The project | 10 min | What is this European project about? Which other countries are working together with us? Presentation of the general goals:
|
| Introduction to topics and dialog | 15 min | Question and interaction to warm up:
Are students more experts than adults in Internet use? Is the Internet mainly a positive or a negative invention? Why? Can we (as adults and educators) support students to prevent and solve problems related to internet misuse? Conclusion and message: The Internet has a great potential for students learning, but can also be a significant source of distraction and risk if not used with awareness, creative and constructive approach. Teachers and educators may have an important role in this field through a variety of strategies of promotion, prevention, and intervention. |
| Overview of the main “web-safety” issues | 15 min | Quick overview (each topic may be associated with a catchy image and a keyword)
Conclusion and message: Why do students take risks on the web? (Because they are in the “exploring” age because they don’t know consequences, because they feel smarter, because they follow the “crowd” or the fashion of the moment, because of lack of EMPATHY…) Conclusion with interaction and message:
(because we don’t know the consequences because we feel smarter because we follow the “crowd”, or the fashion of the moment, lack of EMPATHY…) |
| Cyberbullying | 25 min | Presentation of the topic
What can we do as educators (teachers or parents)?
|
| Project details | 15 min | The activities of the project:
This approach requires not to “blame” (= publicly accuse) the “bully”right away but rather try first to involve him in the problem solution. This is an important point which Teachers and Parents should discuss(especially) and agree on before starting to apply it. |
| Conclusions | 10 min |
|
 |
Duration:
90 minutes |
 |
Aim:
|
| Program | Time | Details |
| The project | 10 min | What is this European project about?Which other countries are working together with us? |
| Introduction to topics and dialog | 15 min | Question and interaction to warm up:
Are students more experts than adults in Internet use? Is the Internet mainly a positive or a negative invention? Why? Can we (as adults and educators) support students to prevent and solve problems related to internet misuse? Conclusion and message: The Internet has a great potential for students learning, but can also be a significant source of distraction and risk if not used with awareness and a creative and constructive approach. Teachers and educators may have an important role in this field through a variety of strategies of promotion, prevention, and intervention. |
| Overview of the main “web-safety” issues | 15 min | Presentation (each topic may be associated with a catchy image and a keyword)
Conclusion and message: Why do students take risks on the web? (Because they don’t know the consequences because they feel smarter because they follow the “crowd”, or the fashion of the moment, lack of EMPATHY…) Conclusion and message: Why do students take risks on the web? (Because they are in the “exploring” age because they don’t know consequences, because they feel smarter, because they follow the “crowd” or the fashion of the moment, because of lack of EMPATHY…) Conclusion with interaction and message:
(because we don’t know the consequences because we feel smarter because we follow the “crowd”, or the fashion of the moment, lack of EMPATHY…) |
| Into Cyberbullying | 25 min | Presentation of the topic
What can we do as educators (teachers or parents)?
can refer to adults if something goes wrong, and they will get help, not blame. Conclusion and message: Cyber-bullying is not a game. It can happen to everyone. Everyone is responsible for stopping / reporting it to reduce the damages. Empathy is a key point: if we put ourselves in the victims´ shoes then we can understand there is no excuse not to act against it. It’s very important that kids know they can talk with adults when something happens: “we all are in the same boat!” |
| Project details | 15 min | The activities of the project:
This approach requires not to “blame” (= publicly accuse)the “bully” right away but try first to involve him in the problem solution. This is an important point which Teacher and Parents should discuss (especially) and agree on before starting to apply it. |
| Conclusions | 10 min |
|
 |
Duration:
30 min |
 |
Target group:
applicable for classes or groups of teachers, 5 – 25 persons |
 |
Aim:
Participants will be stimulated to classify negative behavior patterns into 3 groups: bullying, gray area, no bullying. This is a preparatory activity for the introduction of the definition of (cyber)bullying. It intends to sharpen the ability to distinguish between negative behavior and bullying. |
 |
Materials:
prepared cards, each describing one behavior, moderation cards |
 |
Instruction for implementation:
The facilitators have prepared small cards, each describing a behavior pattern and distribute these among the participants. Depending on the size of the group participants receive one or two cards. They have also prepared moderation cards which will be placed on the ground in order to separate three different fields: Bullying/ Gray area/ no bullying. Participants are asked to read their card aloud and place it into the field they consider correct with a short explanation. Behavior
to damage books, pens … from so. else Evaluation procedure: The facilitator will point out that there will probably be differences in the judgment of the participants what can be identified as bullying. The next step is to introduce the definition of (cyber)bullying, underlining the difference between a conflict/quarrel |
The No Blame Approach (NBA) has been developed in the beginning of the 1990-ties in England by George Robinson, long term headmaster of a school for children with behavioral disorders and Barbara Maines, school psychologist. They were looking for a constructive method to fight bullying in the case of a teenage boy whose teacher had asked them for help as Maines and Robinson describe in their publication: Crying for help – the No Blame Approach to Bullying: “We wanted a strategy that was safe, did not accuse, interrogate or alienate young people. We wanted a process that would improve relationships between young people and the adults working with them.” 1

Up to then different bullying intervention tools have been applied which foresaw severe consequences for the bullying student. However, punishment and negative consequences did not necessarily improve the situation for the bullied child but also carried the danger of revenge. So Barbara Maines and George Robinson designed a concept which did not focus on punishment but rather on the belief that, if group dynamics in a classroom changed – meaning that the bullying actions would no longer be considered cool or funny by the other classmates – the bully will change his behavior and stop bullying.
And the results of the NBA intervention proved that it worked. In most cases the bullying was stopped.
By now the No Blame Approach is used in the following countries: New Zealand, Switzerland, the Netherlands, Belgium and Germany.

The development of the NBA was inspired by the ideas of Thomas Gordon, an US-American clinical psychologist who became well known with his publication: “Parent Effectiveness Training”, a plea for a nonviolent education. It also represents a systemic approach, involving several members of a class in a change process. The systemic approach was introduced by the US-American therapists Steve de Shazer and Insoo Berg and their team at the Brief Family Therapy Center in Milwaukee. The therapists were convinced that individual behavior changes in a system (a group) influence the functioning of the whole group.3 Consequently, a shift in behavior of some group members will have an impact on the other ones. Another important aspect is the future and resource – orientation. The idea is not to look back and not to analyze reasons for behavior patterns. It tries to create a setting which enables looking for solutions. The attitude of the teacher is to initiate a change in behavior. The bullying student will not be confronted with his wrongdoing (“no blame”) but he/she will be integrated into a group process to improve the situation for the victim. Resource orientation means that the bully is not only perceived as a deviant person but also as someone who has shown positive character traits before.
In case of bullying, this process can be initiated by the class teacher or another teacher who knows the class well, a social worker or school psychologist.4 Often the teacher has observed a change in behavior of the bullied student, parents turn to the teacher or bullying activities are reported by others. Since the NBA is working without blame the wording will also be changed, the teacher will address the victim as affected student and bullies will be called protagonists or actors. The process consists of 3 steps:
 No Blame Approach consist of three steps:
No Blame Approach consist of three steps:
7.3.1 Meeting with the affected student
The first meeting with the affected student is crucial. The teacher expresses his/her concern about the situation, assures the student that he/she will take initiative to help him or her and conveys confidence that the situation will change. By doing this the teacher signalizes first of all that he/she knows about the bullying and is determined to intervene.
The teacher informs the parents of the affected student about the intervention (see also comment: Parents and the No Blame Approach). Parents can contribute a lot to the success of the NBA by being positive about it and not insisting on sanctions. Research has shown that parental intervention (addressing the bully themselves or contacting the parents of the bully) leads to an aggravation of the incidents and is most likely contra productive.5
The second step (and most challenging) one is the meeting with the “support group”, consisting of the bully(ies) and colluders/bystanders on the one hand and friendly students on the other hand (6-8 pupils). The students receive an individual invitation for a meeting during classes. There needs to be a close consultation with the teacher whose lesson is concerned. The support group meets in a separate room. Initially, the teacher expresses also here his/her deep concern about the fact that one of the students is being bullied and clarifies that this is an unacceptable situation which needs to be changed. He/she tries to arouse empathy with the affected student. Then he/she is going to ask the students for help to overcome the bullying and addresses them as “experts” for the situation in class. This expresses the explicit difference to other bullying interventions.
This attitude also involves the protagonists, in a setting where it is obvious that the teacher knows who is bothering whom it will not be possible for the bullies to just continue. They are observed by teachers and classmates. But – and this is the big chance for them: stopping the deviant behavior now also means not being punished plus having the chance to re-define their role in class, it is face saving. The teacher explicitly mentions a positive skill each of the students has, including the bullies, focusing on resources rather than on deficits. The next step is to ask the students to come up with concrete ideas how to help/support the affected student X. What can be done? (E.g. walking X home, inviting X, spending time with X…) The teacher takes notes of the ideas on a flipchart/ blackboard and adds the names that are responsible for what. In the case of the protagonist(s), it is sufficient to say: I will stop bothering him/her.
Finally, the teacher thanks the students for their constructive ideas and support and finds a date for follow-up meetings.
The first meeting will be held with the affected student in a separate room.
If the answers are positive, the bullying has stopped and classmates are friendly and supportive the NBA was successful. The teacher will thank the student for the trust and invite him/her to turn to him/her in case of difficulties.
However, if this is not the case, the teacher will announce a second meeting with the support group and assure the student that he/she will continue to take care of the problem.
After the meeting with the affected student the teacher meets the members of the support group individually. He/she asks for an estimate how the affected student is feeling now. Have things improved? What did you notice? Were you able to contribute? Do you have any other ideas what can be done? In case of a positive course (the bullying stopped) the teacher expresses his thankfulness about the constructive role the student played. In case of an unsatisfying development the teacher announces another meeting of the support group in order to reflect the effectiveness of measures and develop new ideas.
Nevertheless, in case of a failure, other measures should be considered.
As pointed out in chapter three, in a cyberbullying case it might be difficult to identify the bullies unless the authorities are contacted to find out the IP address. Also, the provider can be contacted to take down the website. But even in a situation where it is not clear who is the wrongdoer, in the beginning, the No Blame Approach can be applied. A cyberbullying attack can harm the affected student much more since it is a 24/7 harassment visible for anybody in the net.
Sometimes there might be a suspicion who is responsible for the act. in this case, the potential bully should be invited into the group. One possibility is to set a deadline for deleting the offending messages/website (the same day). If the bully is known he/she will also be invited to join the support group. Deleting the message/film/website etc. is mandatory.
If the cyberbullying has caused severe psychological and personal damages further steps need to be taken to stabilize the student (e.g. counseling, therapy).
The fundamental idea of the NBA is to have a tool at hand which significantly improves the possibility to stop bullying. Punitive measures always carry the danger of revenge on the part of the bully, a vicious circle of fear and harm. Measures like swapping the class, especially if the victim is asked to change classes, are disadvantageous for the student.
Ideally, the NBA is not a single tool in school but is embedded in a set of measures e.g. the mediation club, awareness raising activities and other (preventive) programs.
Experiences show that in a lot of cases committed teachers started the implementation of the NBA at their school. After participating in an NBA workshop several steps were initiated to inform the school community.
The headmaster and other teachers will be informed in detail about the steps of the concept, the philosophy of the approach and organizational conditions. The fact that this is a non-punitive tool will certainly provoke discussions amongst the teachers. Often the approach is accepted but not applied by all teachers. If this is the case it is important to ensure a general support of the application even if not every teacher agrees that he/she will work with the NBA. The application can also be delegated to a convinced colleague who knows the class. It should be agreed on that open dissent should not be expressed. However, the support of the headmaster is crucial for a successful implementation.
Sometimes the whole teaching team is interested in participating in the NBA workshop which is an opportunity to fully understand the program.
Many schools have developed their own profile, the “school program”. It might be considered to officially include the NBA and other possible tools of constructive conflict resolution into the school program.
In several countries there are regular meetings of the class teacher and the parents. A meeting is a good opportunity to inform the parents about the introduction of the NBA in case of bullying at school. Sometimes parents are also interested in attending a NBA workshop if possible.
If a meeting is not scheduled for the near future parents should be informed in written form to explain the approach. It is advised to inform the parents of an affected student in a concrete case.
Annalena Scholz, teacher at the Aloisiuskolleg in Bonn: “Before the introduction of the NBA it was important to inform all colleagues and the principal to gain their support. And the concept works. We are able to stop difficult bullying situations. It was also important to explain the approach in detail to the parents of bullied children.”8
What is required: a room where the meeting with the affected student and the support group can take place without interruptions, a flip chart or blackboard, a circle of chairs, duration: Approx. 20 minutes meeting with the affected student, 30 – 40 minutes meeting with the support group.
The NBA is a tool which does not need a lot of preparation. What is essential is a room for the meetings with the affected student and the support group where no interruptions are allowed during the meetings, a corner somewhere in another room is not acceptable. If possible there should be a flipchart or a blackboard where the teacher can collect the ideas of the support group. Everybody should be able to look at each other, so a circle (with or without tables) is a good solution.
There should be close communication between the teacher who will apply the NBA and the teacher who is teaching in class. He/she has to be informed that 6 – 8 students will participate in the support group meeting.
At the end of the chapter interested teachers can find guidelines for the three steps of the concept.
 |
Duration:
7,5 hours including lunch break and short coffee breaks |
 |
Materials: (What is required: depending on the size of the group)
A circle of chairs (no tables), |
 |
Group size:
6 – 10 participants: 1 trainer |
 |
Instruction for implementation:
Multipliers who want to offer a No Blame Approach workshop need to have participated in a workshop before or already have experience in applying the approach, e.g. teachers, social workers. The workshop members can be a team of one school or a mix of teachers (social workers, psychologists) from different schools, sometimes one or two parents are also interested and can be included. Handouts with instructions (e.g. guidelines for the meetings) have to be prepared. An example of a possible structure of a one-day training of the No Blame Approach including samples of flipchart visualizations is added. |
 |
Duration:
1 day |
 |
Group size:
6 – 16 participants/ 1 or 2 trainers |
| Exercise, handout number | Time | Method | Material |
| Welcome, introduction Previous experiences with bullying interventions (positive/negative) |
20 min |
|
Flipcharts: |
| Agenda | 10 min | Flipcharts: |
|
| Understanding bullying How do I recognize bullying? “Bullying glasses” |
40 min | Groups of 2-3 Collection of points on pin board |
Flipcharts:  |
| Definition of (cyber) bullying | 5 min |
Flipcharts:
|
|
| Break | 15 min | ||
| The Bullying system | 30 min | ||
Preparation 1st role play: meeting with the affected student
|
90 min | Groups of 3 | |
| Lunch | 60 min | ||
Preparation 2nd role play: meeting with the support group (H12, H13, H14)
|
120 min | Depending on the group size: 1 or 2 role plays (parallel) |
Handouts: guideline, evaluation Teachers handout 3: Guideline meeting with the support group |
| Break | 15 min | ||
| Follow up meetings with affected student and support group How to continue? |
Flipcharts: 
|
||
| Parents and the NBA Open questions |
Handout: Parents | ||
| Evaluation Goodbye |
Comment: This is a possible agenda for a 1-day-long workshop. If there is more time available, the trainers can include additional activities or exercises (see: Additional material).
 |
Duration:
approx. 20 min |
 |
Aim:
Getting to know each other, participants are sharing their motivation for attendance, reflection of previous experiences with bullying situations. |
 |
Materials:
Flipchart No. 1, (flipchart samples see additional material) |
 |
Instruction for implementation:
After welcoming the participants the facilitators make sure that everyone gets the chance to introduce him/herself in case they have not met the others beforehand. They ask for the motivation to attend the workshop and how long the teachers have been teaching at their school. Next questions:
|
 |
Source:
Further reading:
|
 |
Duration:
Approx. 10 min. |
 |
Aim:
Participants receive an overview of the workshop program and are informed about the relevance of active involvement. |
 |
Materials:
Flipchart No. 2. |
 |
Instruction for implementation:
The facilitators give a brief overview of the workshop agenda.
At the end of the training, participants will discuss possible additional steps to combat further bullying and deal with open questions. |
 |
Duration:
40 min |
||||||||
 |
Aim:
Participants will be introduced to the analytical tool “bullying glasses” in order to recognize a bullying situation. They will sharpen their observation by reflecting possible signs like bullying activities and bullying signals or hints from colleagues, students etc. |
||||||||
 |
Materials: | ||||||||
 |
Instruction for implementation:
The facilitators ask the participants to form small groups of two or three persons in order to reflect the questions on flipchart No. 3 (Approx. 5 minutes).Facilitators have prepared a chart on the pin board:
Facilitators invite the participants to share their collection of answers. One facilitator moderates the exchange and the other one takes notes, classifying the answers and writing them down. There is no discussion at this point, just the collection of answers and the correct classification. If there is no fluent exchange, the trainers try to stimulate further thoughts, e.g.:
Once the columns have been filled in, facilitators introduce the “bullying glasses”, explaining that not only one or two observations/signals/activities justify labeling a certain behavior as bullying. But if a teacher observes several symptoms in different columns there is a strong likelihood for bullying. Also: Once a teacher becomes suspicious that there might be a case of bullying it is helpful to put on the bullying glasses and have a close look at the specific situation of a student. |
 |
Duration:
5 min |
 |
Aim:
On the basis of the definition of bullying and cyberbullying participants will be able to distinguish between a conflict between two or more parties and a bullying situation. |
 |
Materials: |
 |
Instruction for implementation:
After the introduction of the bullying glasses the definition of bullying will be presented. In this context, the facilitators emphasize that bullying is not a case for peer mediation since there is an extreme power imbalance between the protagonists.
|
 |
Duration:
10 min |
 |
Aim:
Participants are introduced to the basic idea of a systemic approach, meaning that bullying is a group phenomenon which involves protagonists (the bully or bullies), colluders, bystanders, and observers. It is a functioning destructive system of a group which needs an intervention from the outside in order to change the situation for the better. Participants understand that the bullied person is hardly ever able to disburden him/herself. |
 |
Materials:
Flipchart No. 5 |
 |
Instruction for implementation:
The facilitators present bullying as a closed system with different roles. There are protagonists (the bully or bullies), colluders, bystanders, and observers. Since there is an extreme power imbalance between the bullies and the bullied student, an intervention from outside is necessary. The facilitators point out that bullying will not be regarded from the perspective of the offender and the victim but rather from a systemic approach. This means that representatives of the class will be in the focus including the protagonists, colluders, and observers as well as the affected student. Bullying is a group phenomenon. |
 |
Duration:
10 min |
 |
Aim:
Participants get to know the “special” attitude of the NBA. Contrary to common educational interventions in case of bullying the teacher will not blame the bully/bullies but rather involve him/them and other students in a process of behavior change, thus initiating a supportive structure for the bullied student and an end of bullying activities. |
 |
Materials:
Flipchart No. 6 |
 |
Instruction for implementation:
Facilitators explain the characteristics of the NBA. There is possibly a need to discuss the aspect: “no blame, no punishment” since this contradicts the usual educational responses. If participants are very critical it is helpful to talk about bullying cases where the offender was punished and might have taken revenge or where a bullied student left the class, in both cases a win-lose result. The NBA tries to change behavior patterns by influencing group dynamics and thus withdrawing a supportive atmosphere for the bullying protagonists. |
 |
Background information:
The concept was developed by George Robinson and Barbara Maines in the 1990-ies in England. In 2002 Christopher Szaday introduced it in Switzerland since 2003 Heike Blum and Detlef Beck from the German organization Fairaend have been spreading the approach in Germany.Furthermore, the concept is in use in the Netherlands, Belgium, Luxembourg, Australia and New Zealand. |
 |
Duration:
10 min |
 |
Aim:
Participants will be introduced to the steps of the NBA approach and get an idea about the concrete procedure. |
 |
Materials: |
 |
Instruction for implementation:
The facilitators point out that these two flipcharts give an overview of the NBA procedure. The facilitators comment on the illustrated steps: Firstly, the teacher meets with the affected student in order to win his/her trust and his/her agreement to intervene. This meeting is crucial, the teacher should not only show concern about what is happening but also his/her commitment to help and confidence that the problem can be solved. The student will be informed about the planned steps. In order to form the support group the teacher asks the names of friends and of classmates who are still supportive. On the other hand, he/she asks who is bothering the affected student (offender and bystanders). The goal of this meeting is not
The meeting lasts 30 – 45 minutes. The student should be relieved of any responsibility, the teacher signals his/her commitment. A date for a follow-up meeting will be found (within 8 – 14 days), until then the student observes carefully what happens. Secondly, the teacher forms a support group. This group includes 3 – 4 bullying protagonists plus 3 – 4 friends of the affected student or at least neutral students.The group´s unique factor is that it is not a support group for the affected student but for the teacher who asks for help to solve the bullying problem.The support group aims at developing ideas and measures which can be carried out by members of the group to stop bullying activities. The meeting with the support group will take place during regular classes (colleagues need to be informed beforehand). Students will be invited personally or in written form, the purpose of the meeting will not be mentioned, just the need for solving a problem together. The teacher shows an appreciative attitude towards all participants without blaming anybody and mentions skills and resources each and every student has to help. Thirdly, follow up meetings with the affected student and members of the support group (individually) will take place 8 – 14 days later. The teacher talks to the affected student in order to find out whether any (positive) changes occurred and how he/she is doing.There will also be individual meetings with the group members to evaluate the situation. Have the students been able to put their ideas into practice? Has the bullying stopped? At this point, the facilitators don´t allow a lot of questions. Open questions can be answered later on when the steps will be dealt with in detail. |
The concept was developed by George Robinson and Barbara Maines in the 1990-ies in England. In 2002 Christopher Szaday introduced it in Switzerland since 2003 Heike Blum and Detlef Beck from the German organization Fairaend have been spreading the approach in Germany.Furthermore, the concept is in use in the Netherlands, Belgium, Luxembourg, Australia and New Zealand.
 |
Duration:
15 min |
 |
Aim:
Participants receive a detailed overview how to approach a bullied student including a possible interview guide. |
 |
Materials:
Flipcharts No. 9, 10, 11, 12 – fastened on a pin board next to each other |
 |
Instruction for implementation:
The facilitators explain that the group is now at the point to actually start with the training of the 3 steps of the concept. The first step is to meet with the affected student. Depending on the situation the teacher will call the student at home (if he/she is not going to school anymore) or contact him/her in school. The meeting will be arranged in a separate room where nobody will disturb them. The teacher greets the student warmly: “How nice to see you. Don´t worry I´m not talking about the lessons that you missed during the last days…” He/she will share his/her observations: “I have noticed that…” In the next phase, the teacher asks how the student feels at school. It is not necessary to go into details of the bullying incidents but rather to get a general idea. The teacher will question the student concerning his/her will to change the situation, will convey confidence and express his/her commitment to help. Flipchart No. 11 The teacher explains the next steps, emphasizes that he/she wants to relieve the burden and conveys safety. Flipchart No. 12 Next, the teacher will inquire the names of friends or companions of the affected student but also the names of the bullying protagonists. Afterward, he/she assures confidentiality and finds out what should not be mentioned. Finally, the student is asked for his/her approval to proceed and a date for a follow- up meeting is agreed on.At the end of the presentation of the guideline for the talk, the facilitators will underline that it is of utmost importance to create an atmosphere of trust and confidence during the whole conversation. |